RE_0">楚慧杯初赛——RE复现
Level_One
这里发现还是jeb好用
java">package com.example.mobile1;
import android.os.Bundle;
import android.view.View.OnClickListener;
import android.view.View;
import android.widget.Button;
import android.widget.EditText;
import android.widget.Toast;
import androidx.appcompat.app.AppCompatActivity;
import java.nio.charset.StandardCharsets;
public class MainActivity extends AppCompatActivity {
Button check;
EditText flag;
String input;
private String Encrypt(byte[] arg12) {
String v0 = this.getResources().getString(0x7F0E006C); // string:table "n4/Xv90ElB32S6MmyK+iVIgkjU17CDGaLYxeuzsc8TqNOtrJWPfRp=HFhAwdb5oZQ"
StringBuilder v1 = new StringBuilder();
int[] v3 = new int[4];
int v4 = arg12.length - arg12.length % 3;
int v7;
for(v7 = 0; v7 < v4; v7 += 3) {
int v8 = 0;
int v9 = 0;
while(v8 < 3) {
v9 = v9 << 8 | arg12[v7 + v8] & 0xFF;
++v8;
}
int v8_1;
for(v8_1 = 0; v8_1 < 4; ++v8_1) {
v3[v8_1] = v9 & 0x3F;
v9 >>= 6;
}
int v8_2;
for(v8_2 = 3; v8_2 >= 0; --v8_2) {
v1.append(((char)v0.charAt(v3[v8_2])));
}
}
int v3_1 = arg12.length % 3;
if(v3_1 == 1) {
v1.append(((char)v0.charAt(arg12[arg12.length - 1] >> 2)));
v1.append(((char)v0.charAt((arg12[arg12.length - 1] & 3) << 4)));
v1.append("%&");
}
else if(v3_1 == 2) {
v1.append(((char)v0.charAt(arg12[arg12.length - 2] >> 2)));
v1.append(((char)v0.charAt(arg12[arg12.length - 1] >> 4 | (arg12[arg12.length - 2] & 3) << 4)));
v1.append(((char)v0.charAt((arg12[arg12.length - 1] & 15) << 2)));
v1.append('*');
return v1.toString();
}
return v1.toString();
}
@Override // androidx.fragment.app.FragmentActivity
protected void onCreate(Bundle arg2) {
super.onCreate(arg2);
this.setContentView(0x7F0B001C); // layout:activity_main
this.flag = (EditText)this.findViewById(0x7F0800C0); // id:input
Button v2 = (Button)this.findViewById(0x7F080060); // id:check_flag
this.check = v2;
v2.setOnClickListener(new View.OnClickListener() {
@Override // android.view.View$OnClickListener
public void onClick(View arg3) {
MainActivity.this.input = MainActivity.this.flag.getText().toString();
if(MainActivity.this.Encrypt(MainActivity.this.input.getBytes(StandardCharsets.UTF_8)).equals(MainActivity.this.getString(0x7F0E0025))) { // string:enc "UsPYUFORMXnHSXIe6xpFSilR2iKs6RvtjeVFSfpHSX9zM0Sp6XVFjeK5"
Toast.makeText(MainActivity.this, "you got it", 1).show();
return;
}
Toast.makeText(MainActivity.this, "error, try hard", 1).show();
}
});
}
}
一眼魔改Base系列
import base64
string_table="n4/Xv90ElB32S6MmyK+iVIgkjU17CDGaLYxeuzsc8TqNOtrJWPfRp=HFhAwdb5oZQ"
enc='UsPYUFORMXnHSXIe6xpFSilR2iKs6RvtjeVFSfpHSX9zM0Sp6XVFjeK5'
# -*- coding: utf-8
import base64
STANDARD_ALPHABET = b'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/x'
CUSTOM_ALPHABET = b'n4/Xv90ElB32S6MmyK+iVIgkjU17CDGaLYxeuzsc8TqNOtrJWPfRp=HFhAwdb5oZQ'
ENCODE_TRANS = bytes.maketrans(STANDARD_ALPHABET, CUSTOM_ALPHABET)
DECODE_TRANS = bytes.maketrans(CUSTOM_ALPHABET, STANDARD_ALPHABET)
def encode(input):
return base64.b64encode(input).translate(ENCODE_TRANS)
def decode(input):
return base64.b64decode(input.translate(DECODE_TRANS))
destr = decode(enc)
print(destr.decode()) #flag{380605c6-7123-4f71-b573-601e8c4457b4}
Level_Up
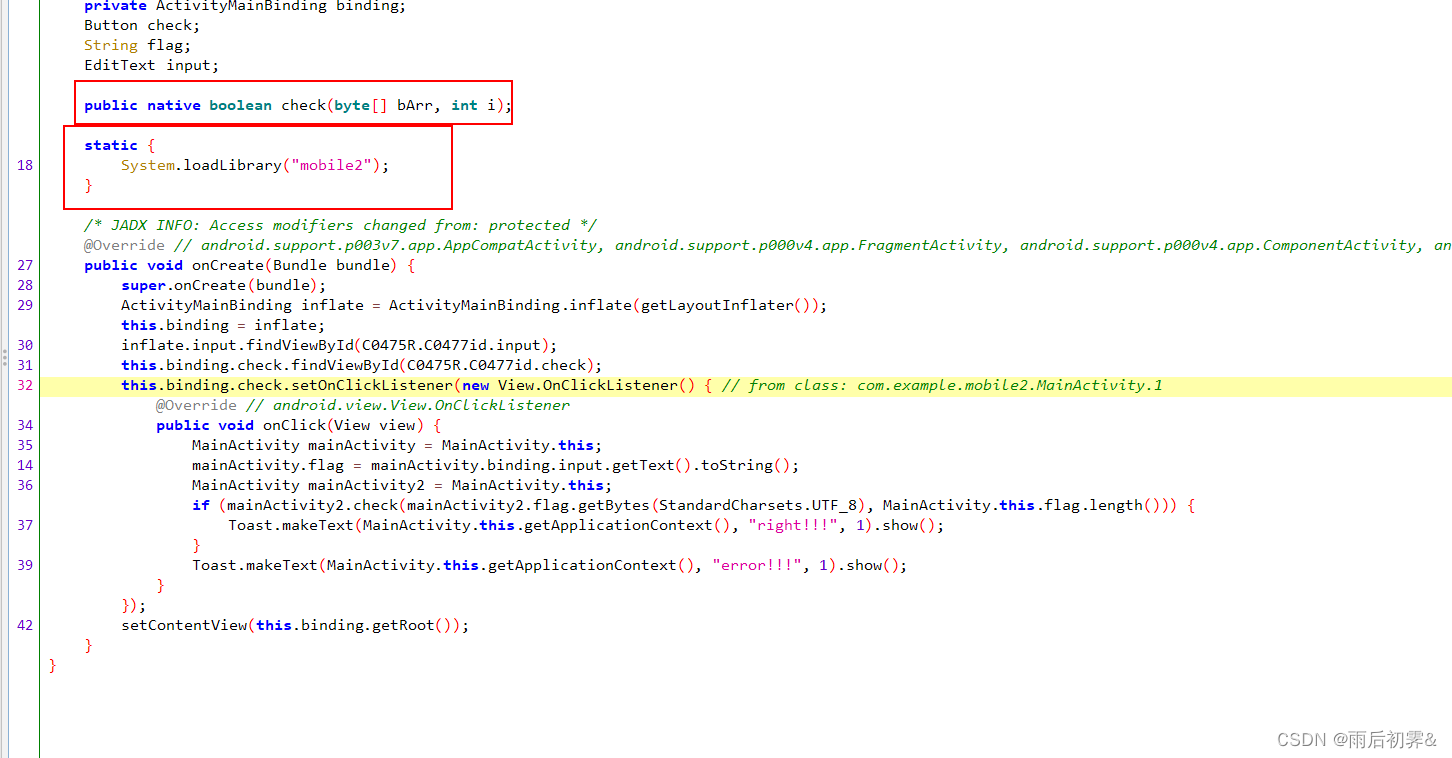
重点是SO文件
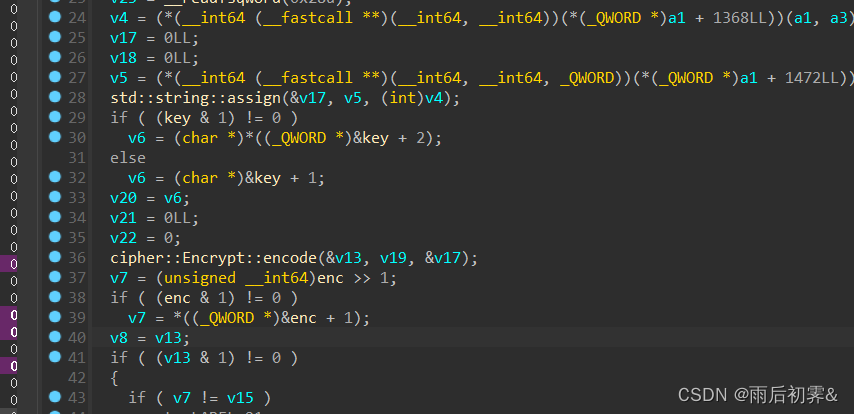
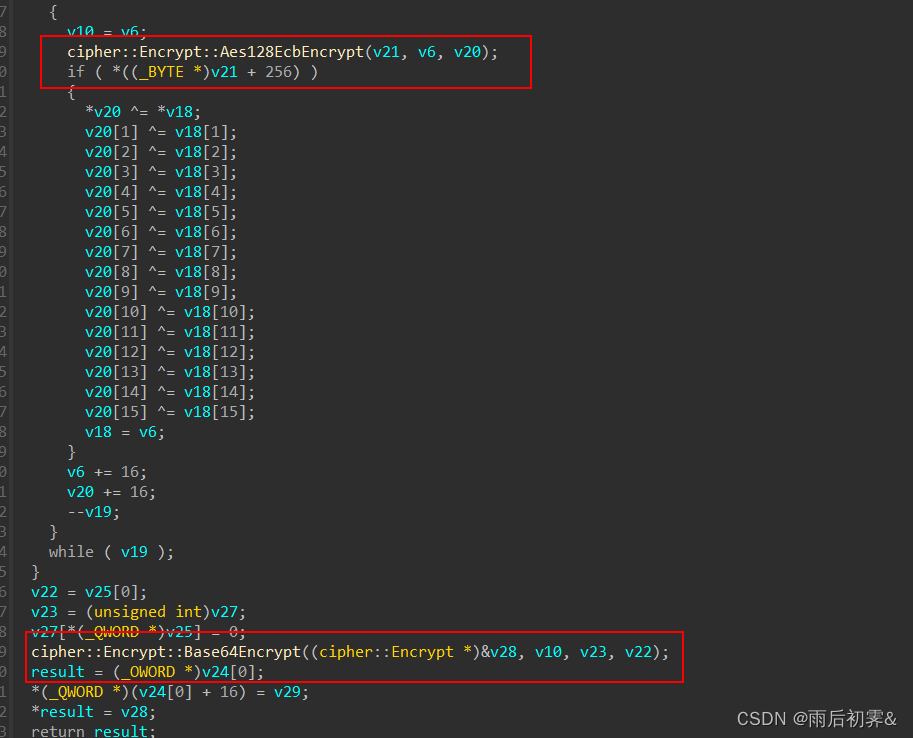
key和enc都给出,看加密
EXP
enc=b'gOuWlCTi+hhzCn6rWxDm8IuuBwiOtM+V/m39bthXTeT3E6WYrLU0CDqG76Kvpkmc'
key=b'followyourheart!'
import base64
tmep_string=base64.b64decode(enc)
print(tmep_string)
from Crypto.Cipher import AES
aes = AES.new(key,AES.MODE_ECB) #创建一个aes对象
den_text = aes.decrypt(tmep_string) # 解密密文
print(den_text)
#b'flag{6b1df900-1284-11ed-9fa7-5405dbe5e745}\x06\x06\x06\x06\x06\x06'
ezevem
__int64 __fastcall main(int a1, char **a2, char **a3)
{
int v4; // [rsp+4h] [rbp-DCh]
int i; // [rsp+8h] [rbp-D8h]
int j; // [rsp+Ch] [rbp-D4h]
int enc[40]; // [rsp+10h] [rbp-D0h]
__int64 v8[4]; // [rsp+B0h] [rbp-30h] BYREF
int v9; // [rsp+D0h] [rbp-10h]
__int16 v10; // [rsp+D4h] [rbp-Ch]
char v11; // [rsp+D6h] [rbp-Ah]
unsigned __int64 v12; // [rsp+D8h] [rbp-8h]
v12 = __readfsqword(0x28u);
memset(v8, 0, sizeof(v8));
v9 = 0;
v10 = 0;
v11 = 0;
enc[38] = 0;
enc[0] = 138;
enc[1] = 144;
enc[2] = 131;
enc[3] = 137;
enc[4] = 125;
enc[5] = 136;
enc[6] = 131;
enc[7] = 52;
enc[8] = 135;
enc[9] = 134;
enc[10] = 135;
enc[11] = 51;
enc[12] = 134;
enc[13] = 57;
enc[14] = 56;
enc[15] = 55;
enc[16] = 134;
enc[17] = 135;
enc[18] = 58;
enc[19] = 58;
enc[20] = 54;
enc[21] = 60;
enc[22] = 54;
enc[23] = 56;
enc[24] = 51;
enc[25] = 138;
enc[26] = 136;
enc[27] = 53;
enc[28] = 59;
enc[29] = 134;
enc[30] = 60;
enc[31] = 52;
enc[32] = 52;
enc[33] = 55;
enc[34] = 53;
enc[35] = 54;
enc[36] = 54;
enc[37] = 127;
v4 = 0;
printf("plz enter flag: ");
__isoc99_scanf("%s", v8);
for ( i = 0; i <= 37; ++i )
input[i] = *((char *)v8 + i);
while ( opt[v4] )
{
switch ( opt[v4] )
{
case 1u:
Xor(opt[v4 + 1], opt[v4 + 2]);
break;
case 2u:
Add(opt[v4 + 1], opt[v4 + 2]);
break;
case 3u:
Sub(opt[v4 + 1], opt[v4 + 2]);
break;
case 4u:
Left(opt[v4 + 1], opt[v4 + 2]); // temp[opt[v4 + 1]] <<= temp[opt[v4 + 2]];
break;
case 5u:
Right(opt[v4 + 1], opt[v4 + 2]); // temp[a1] = (int)temp[a1] >> temp[a2];
break;
case 6u:
SetInput(opt[v4 + 1], opt[v4 + 2]); // input[a1] = temp[a2];
break;
case 7u:
GetInput(opt[v4 + 1], opt[v4 + 2]); // temp[a1] = input[a2];
break;
case 8u:
SetTemp(opt[v4 + 1], opt[v4 + 2]); // temp[a1] = a2;
break;
default:
break;
}
v4 += 3;
}
for ( j = 0; j <= 37; ++j )
{
if ( enc[j] != input[j + 50] )
exit(0);
}
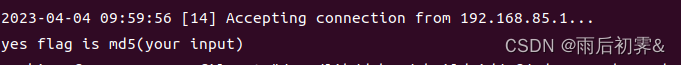
printf("yes flag is %s", (const char *)v8);
return 0LL;
}
拿到输出
temp[1]= 17;
temp[2]= 19;
temp[0] = szInput[0];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[0] = temp[0];
temp[0] = szInput[1];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[1] = temp[0];
temp[0] = szInput[2];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[2] = temp[0];
temp[0] = szInput[3];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[3] = temp[0];
temp[0] = szInput[4];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[4] = temp[0];
temp[0] = szInput[5];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[5] = temp[0];
temp[0] = szInput[6];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[6] = temp[0];
temp[0] = szInput[7];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[7] = temp[0];
temp[0] = szInput[8];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[8] = temp[0];
temp[0] = szInput[9];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[9] = temp[0];
temp[0] = szInput[10];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[10] = temp[0];
temp[0] = szInput[11];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[11] = temp[0];
temp[0] = szInput[12];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[12] = temp[0];
temp[0] = szInput[13];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[13] = temp[0];
temp[0] = szInput[14];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[14] = temp[0];
temp[0] = szInput[15];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[15] = temp[0];
temp[0] = szInput[16];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[16] = temp[0];
temp[0] = szInput[17];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[17] = temp[0];
temp[0] = szInput[18];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[18] = temp[0];
temp[0] = szInput[19];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[19] = temp[0];
temp[0] = szInput[20];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[20] = temp[0];
temp[0] = szInput[21];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[21] = temp[0];
temp[0] = szInput[22];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[22] = temp[0];
temp[0] = szInput[23];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[23] = temp[0];
temp[0] = szInput[24];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[24] = temp[0];
temp[0] = szInput[25];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[25] = temp[0];
temp[0] = szInput[26];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[26] = temp[0];
temp[0] = szInput[27];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[27] = temp[0];
temp[0] = szInput[28];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[28] = temp[0];
temp[0] = szInput[29];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[29] = temp[0];
temp[0] = szInput[30];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[30] = temp[0];
temp[0] = szInput[31];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[31] = temp[0];
temp[0] = szInput[32];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[32] = temp[0];
temp[0] = szInput[33];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[33] = temp[0];
temp[0] = szInput[34];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[34] = temp[0];
temp[0] = szInput[35];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[35] = temp[0];
temp[0] = szInput[36];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[36] = temp[0];
temp[0] = szInput[37];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[37] = temp[0];
这里其实是异或再加,
使用z3
enc=[138, 144, 131, 137, 125, 136, 131, 52, 135, 134, 135, 51, 134, 57, 56, 55, 134, 135, 58, 58, 54, 60, 54, 56, 51, 138, 136, 53, 59, 134, 60, 52, 52, 55, 53, 54, 54, 127, 0]
from z3 import *
s=Solver()
szInput=[BitVec(f'{i}',64) for i in range(38)]
for i in szInput:
s.add(i<127)
s.add(i>0)
temp=[0]*38
temp[1]= 17;
temp[2]= 19;
temp[0] = szInput[0];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[0] = temp[0];
temp[0] = szInput[1];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[1] = temp[0];
temp[0] = szInput[2];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[2] = temp[0];
temp[0] = szInput[3];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[3] = temp[0];
temp[0] = szInput[4];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[4] = temp[0];
temp[0] = szInput[5];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[5] = temp[0];
temp[0] = szInput[6];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[6] = temp[0];
temp[0] = szInput[7];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[7] = temp[0];
temp[0] = szInput[8];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[8] = temp[0];
temp[0] = szInput[9];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[9] = temp[0];
temp[0] = szInput[10];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[10] = temp[0];
temp[0] = szInput[11];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[11] = temp[0];
temp[0] = szInput[12];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[12] = temp[0];
temp[0] = szInput[13];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[13] = temp[0];
temp[0] = szInput[14];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[14] = temp[0];
temp[0] = szInput[15];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[15] = temp[0];
temp[0] = szInput[16];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[16] = temp[0];
temp[0] = szInput[17];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[17] = temp[0];
temp[0] = szInput[18];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[18] = temp[0];
temp[0] = szInput[19];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[19] = temp[0];
temp[0] = szInput[20];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[20] = temp[0];
temp[0] = szInput[21];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[21] = temp[0];
temp[0] = szInput[22];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[22] = temp[0];
temp[0] = szInput[23];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[23] = temp[0];
temp[0] = szInput[24];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[24] = temp[0];
temp[0] = szInput[25];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[25] = temp[0];
temp[0] = szInput[26];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[26] = temp[0];
temp[0] = szInput[27];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[27] = temp[0];
temp[0] = szInput[28];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[28] = temp[0];
temp[0] = szInput[29];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[29] = temp[0];
temp[0] = szInput[30];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[30] = temp[0];
temp[0] = szInput[31];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[31] = temp[0];
temp[0] = szInput[32];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[32] = temp[0];
temp[0] = szInput[33];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[33] = temp[0];
temp[0] = szInput[34];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[34] = temp[0];
temp[0] = szInput[35];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[35] = temp[0];
temp[0] = szInput[36];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[36] = temp[0];
temp[0] = szInput[37];
temp[0] ^= temp[1];
temp[0] += temp[2];
szInput[37] = temp[0];
for i in range(38):
s.add(szInput[i]==enc[i])
print(s.check())
if s.check()==sat:
m=s.model()
inp=[BitVec(f'{i}',64) for i in range(38)]
for i in inp:
print(chr(m[i].as_long()),end='')
#sat
#flag{da0ebe1b745be6628241fd39b8005322}
crackMe
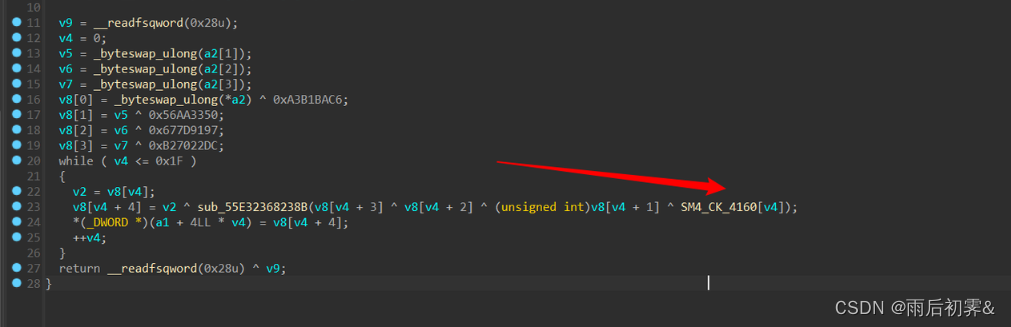
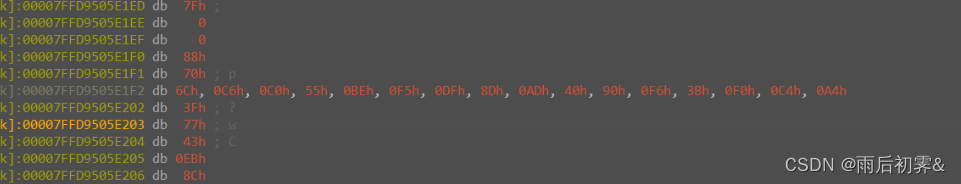
多次调试后发现密文,密文提取
SM4脚本:https://ppppz.net/2022/02/03/SM4-P-Z/
再直接AES解密就行
// chb.cpp : 此文件包含 "main" 函数。程序执行将在此处开始并结束。
//
#include <stdio.h>
#include <string.h>
#include "SM4.h"
int main()
{
unsigned char key[16] =
{
0x00, 0x01, 0x02, 0x03, 0x04, 0x05, 0x06, 0x07, 0x08, 0x09, 0x0A, 0x0B, 0x0C, 0x0D, 0x0E, 0x0F };
unsigned char output[16] =
{
0x6C, 0xC6, 0xC0, 0x55, 0xBE, 0xF5, 0xDF, 0x8D, 0xAD, 0x40, 0x90, 0xF6, 0x3B, 0xF0, 0xC4, 0xA4
};
Context ctx;
int i;
SetKeyDec(&ctx, key);
CryptEBC(&ctx, 0, 16, output, output);
for (i = 0; i < 16; i++)
printf("0x%x,", output[i]);
return 0;
}
key=[0x00, 0x01, 0x02, 0x03, 0x04, 0x05, 0x06, 0x07, 0x08, 0x09, 0x0A, 0x0B, 0x0C, 0x0D, 0x0E, 0x0F]
enc=[0x1d,0x95,0x3d,0x55,0x1c,0xa,0x27,0xeb,0xe0,0xe2,0x81,0xab,0xc1,0x43,0x32,0x29]
from Crypto.Cipher import AES
aes = AES.new(bytes(key),AES.MODE_ECB) #创建一个aes对象
den_text = aes.decrypt(bytes(enc)) # 解密密文
print(den_text)
import hashlib
s='8c1a2110398ff814'
print(hashlib.md5(s.encode()).hexdigest())
find_the_way
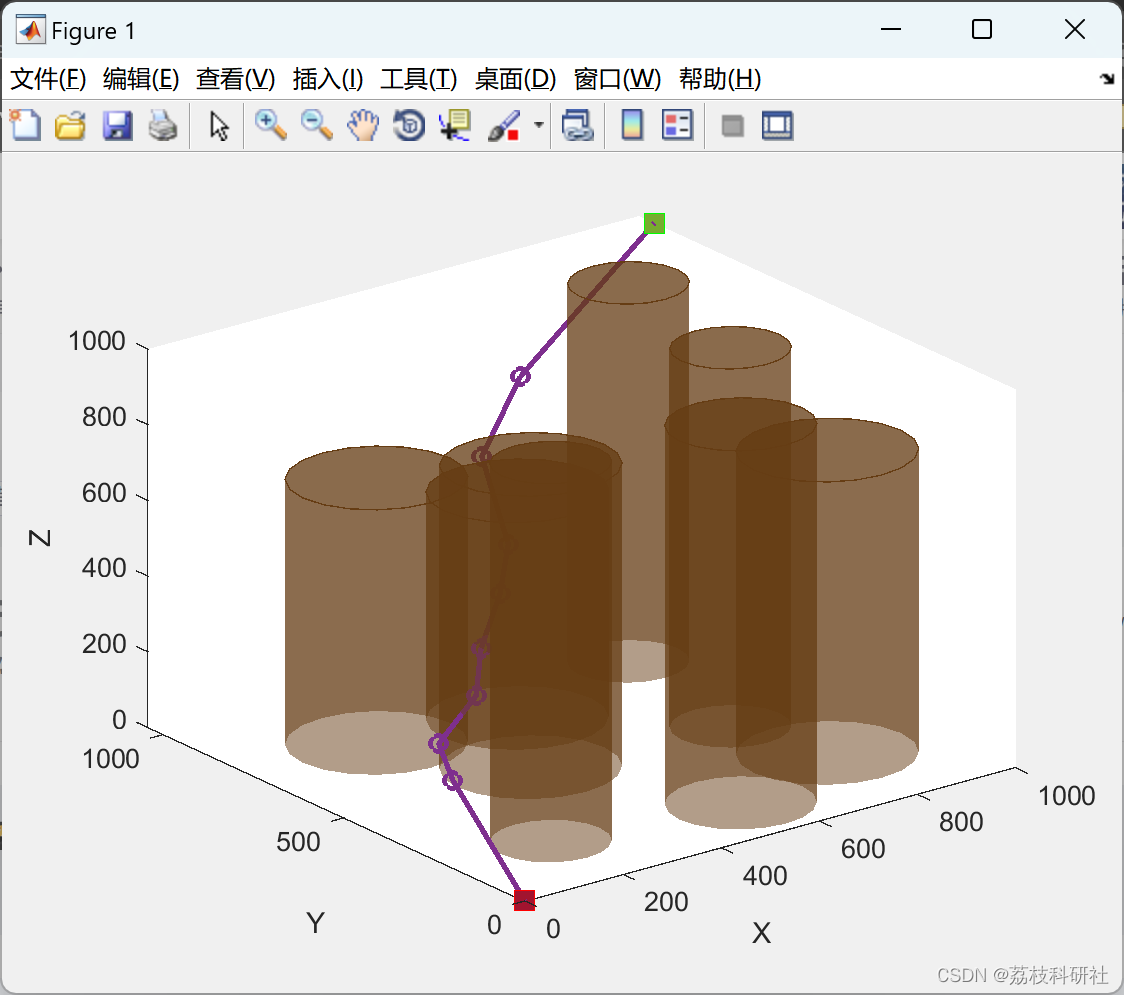
有别与数组迷宫题,RE首先放这题,感觉很简单但当时没做出来。
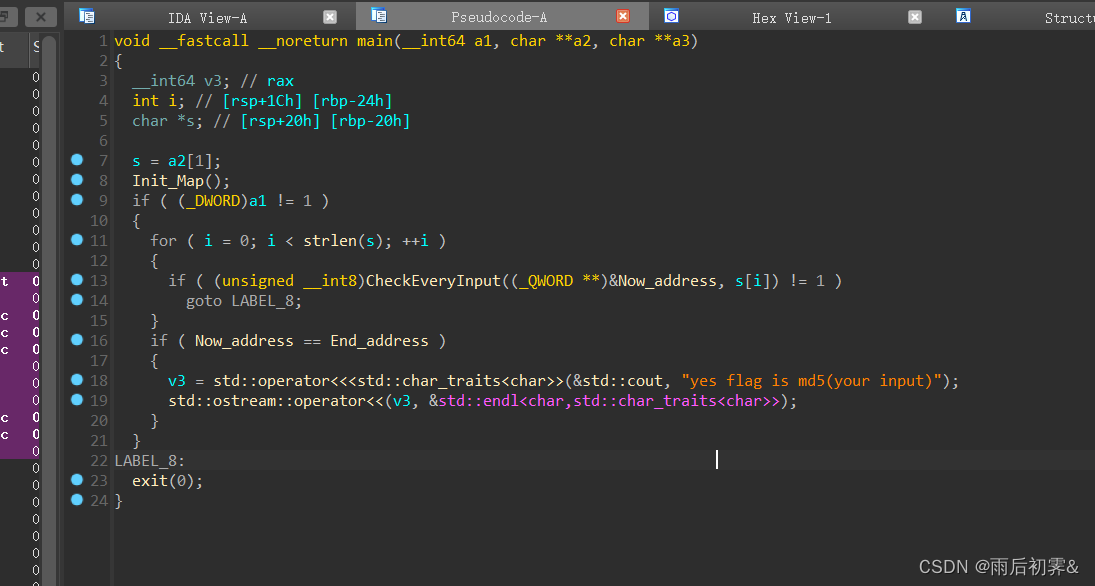
输入从环境里面拿的,这里记得附加就行
这里Map的一个单元是在堆里面的
我们可以解释为一个结构体
typedef long long QWORD;
struct tagMap {
QWORD m_QPre_address;
QWORD m_QNext_address;
QWORD m_QNext_address2;
char szarray[8];
QWORD Unuse;
QWORD Unuse2;
};
根据判断
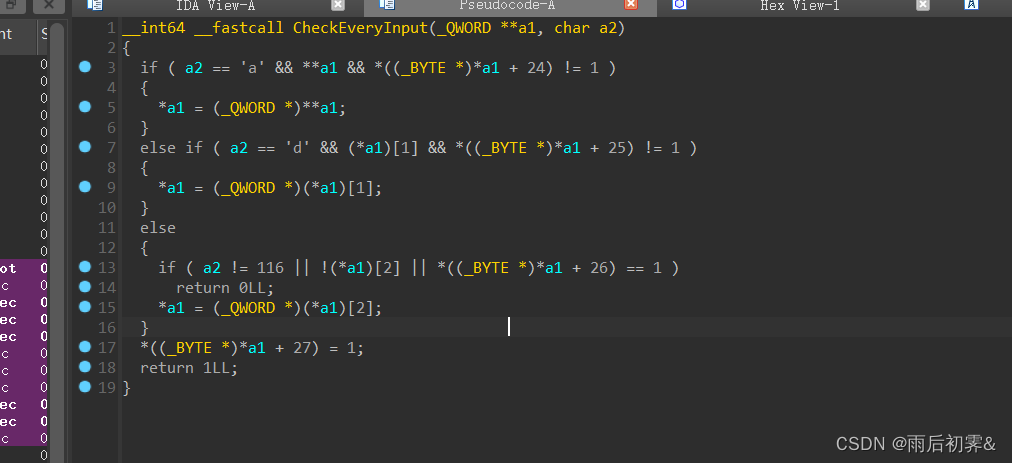
后面的 Unuse,Unuse2到不是很重要
主要是看
QWORD m_QPre_address; //上一个地址 a
QWORD m_QNext_address; //下一个地址 d
QWORD m_QNext_address2;//下一个地址2 t
// szarray 前3个 代表有没有路 1为有路,0为无路
szarray[0];
szarray[1];
szarray[2];
szarray[3];
把堆全copy下来,写递归解就行
Num_map=[0x000055CD7A81DF10, 0x000055CD7A81DF40, 0x000055CD7A81DFD0, 0x000055CD7A81E0C0, 0x000055CD7A81E210, 0x000055CD7A81E3C0, 0x000055CD7A81E5D0, 0x000055CD7A81E840, 0x000055CD7A81EB10, 0x000055CD7A81EE40, 0x0000000000000000, 0x0000000000000031, 0x0000000000000000, 0x0000000000000000, 0x000055CD7A81DF70, 0x0000000000000101, 0x0000000000000000, 0x0000000000000031, 0x0000000000000000, 0x000055CD7A81DF70, 0x000055CD7A81E000, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81DF40, 0x000055CD7A81DFA0, 0x000055CD7A81DF10, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81DF70, 0x0000000000000000, 0x000055CD7A81E060, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x0000000000000000, 0x000055CD7A81E000, 0x000055CD7A81E0F0, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81DFD0, 0x000055CD7A81E030, 0x000055CD7A81DF40, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E000, 0x000055CD7A81E060, 0x000055CD7A81E150, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E030, 0x000055CD7A81E090, 0x000055CD7A81DFA0, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E060, 0x0000000000000000, 0x000055CD7A81E1B0, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x0000000000000000, 0x000055CD7A81E0F0, 0x000055CD7A81E240, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E0C0, 0x000055CD7A81E120, 0x000055CD7A81DFD0, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E0F0, 0x000055CD7A81E150, 0x000055CD7A81E2A0, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E120, 0x000055CD7A81E180, 0x000055CD7A81E030, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E150, 0x000055CD7A81E1B0, 0x000055CD7A81E300, 0x0000000000010001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E180, 0x000055CD7A81E1E0, 0x000055CD7A81E090, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E1B0, 0x0000000000000000, 0x000055CD7A81E360, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x0000000000000000, 0x000055CD7A81E240, 0x000055CD7A81E3F0, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E210, 0x000055CD7A81E270, 0x000055CD7A81E0C0, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E240, 0x000055CD7A81E2A0, 0x000055CD7A81E450, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E270, 0x000055CD7A81E2D0, 0x000055CD7A81E120, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E2A0, 0x000055CD7A81E300, 0x000055CD7A81E4B0, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E2D0, 0x000055CD7A81E330, 0x000055CD7A81E180, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E300, 0x000055CD7A81E360, 0x000055CD7A81E510, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E330, 0x000055CD7A81E390, 0x000055CD7A81E1E0, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E360, 0x0000000000000000, 0x000055CD7A81E570, 0x0000000000010100, 0x0000000000000000, 0x0000000000000031, 0x0000000000000000, 0x000055CD7A81E3F0, 0x000055CD7A81E600, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E3C0, 0x000055CD7A81E420, 0x000055CD7A81E210, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E3F0, 0x000055CD7A81E450, 0x000055CD7A81E660, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E420, 0x000055CD7A81E480, 0x000055CD7A81E270, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E450, 0x000055CD7A81E4B0, 0x000055CD7A81E6C0, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E480, 0x000055CD7A81E4E0, 0x000055CD7A81E2D0, 0x0000000000010100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E4B0, 0x000055CD7A81E510, 0x000055CD7A81E720, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E4E0, 0x000055CD7A81E540, 0x000055CD7A81E330, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E510, 0x000055CD7A81E570, 0x000055CD7A81E780, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E540, 0x000055CD7A81E5A0, 0x000055CD7A81E390, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E570, 0x0000000000000000, 0x000055CD7A81E7E0, 0x0000000000010100, 0x0000000000000000, 0x0000000000000031, 0x0000000000000000, 0x000055CD7A81E600, 0x000055CD7A81E870, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E5D0, 0x000055CD7A81E630, 0x000055CD7A81E3C0, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E600, 0x000055CD7A81E660, 0x000055CD7A81E8D0, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E630, 0x000055CD7A81E690, 0x000055CD7A81E420, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E660, 0x000055CD7A81E6C0, 0x000055CD7A81E930, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E690, 0x000055CD7A81E6F0, 0x000055CD7A81E480, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E6C0, 0x000055CD7A81E720, 0x000055CD7A81E990, 0x0000000000010100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E6F0, 0x000055CD7A81E750, 0x000055CD7A81E4E0, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E720, 0x000055CD7A81E780, 0x000055CD7A81E9F0, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E750, 0x000055CD7A81E7B0, 0x000055CD7A81E540, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E780, 0x000055CD7A81E7E0, 0x000055CD7A81EA50, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E7B0, 0x000055CD7A81E810, 0x000055CD7A81E5A0, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E7E0, 0x0000000000000000, 0x000055CD7A81EAB0, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x0000000000000000, 0x000055CD7A81E870, 0x000055CD7A81EB40, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E840, 0x000055CD7A81E8A0, 0x000055CD7A81E5D0, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E870, 0x000055CD7A81E8D0, 0x000055CD7A81EBA0, 0x0000000000000101, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E8A0, 0x000055CD7A81E900, 0x000055CD7A81E630, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E8D0, 0x000055CD7A81E930, 0x000055CD7A81EC00, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E900, 0x000055CD7A81E960, 0x000055CD7A81E690, 0x0000000000010100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E930, 0x000055CD7A81E990, 0x000055CD7A81EC60, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E960, 0x000055CD7A81E9C0, 0x000055CD7A81E6F0, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E990, 0x000055CD7A81E9F0, 0x000055CD7A81ECC0, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E9C0, 0x000055CD7A81EA20, 0x000055CD7A81E750, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81E9F0, 0x000055CD7A81EA50, 0x000055CD7A81ED20, 0x0000000000000101, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EA20, 0x000055CD7A81EA80, 0x000055CD7A81E7B0, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EA50, 0x000055CD7A81EAB0, 0x000055CD7A81ED80, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EA80, 0x000055CD7A81EAE0, 0x000055CD7A81E810, 0x0000000000010001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EAB0, 0x0000000000000000, 0x000055CD7A81EDE0, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x0000000000000000, 0x000055CD7A81EB40, 0x000055CD7A81EE70, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EB10, 0x000055CD7A81EB70, 0x000055CD7A81E840, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EB40, 0x000055CD7A81EBA0, 0x000055CD7A81EED0, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EB70, 0x000055CD7A81EBD0, 0x000055CD7A81E8A0, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EBA0, 0x000055CD7A81EC00, 0x000055CD7A81EF30, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EBD0, 0x000055CD7A81EC30, 0x000055CD7A81E900, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EC00, 0x000055CD7A81EC60, 0x000055CD7A81EF90, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EC30, 0x000055CD7A81EC90, 0x000055CD7A81E960, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EC60, 0x000055CD7A81ECC0, 0x000055CD7A81EFF0, 0x0000000000010100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EC90, 0x000055CD7A81ECF0, 0x000055CD7A81E9C0, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81ECC0, 0x000055CD7A81ED20, 0x000055CD7A81F050, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81ECF0, 0x000055CD7A81ED50, 0x000055CD7A81EA20, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81ED20, 0x000055CD7A81ED80, 0x000055CD7A81F0B0, 0x0000000000010100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81ED50, 0x000055CD7A81EDB0, 0x000055CD7A81EA80, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81ED80, 0x000055CD7A81EDE0, 0x000055CD7A81F110, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EDB0, 0x000055CD7A81EE10, 0x000055CD7A81EAE0, 0x0000000000000100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EDE0, 0x0000000000000000, 0x000055CD7A81F170, 0x0000000000000101, 0x0000000000000000, 0x0000000000000031, 0x0000000000000000, 0x000055CD7A81EE70, 0x0000000000000000, 0x0000000000010001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EE40, 0x000055CD7A81EEA0, 0x000055CD7A81EB10, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EE70, 0x000055CD7A81EED0, 0x0000000000000000, 0x0000000000010100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EEA0, 0x000055CD7A81EF00, 0x000055CD7A81EB70, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EED0, 0x000055CD7A81EF30, 0x0000000000000000, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EF00, 0x000055CD7A81EF60, 0x000055CD7A81EBD0, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EF30, 0x000055CD7A81EF90, 0x0000000000000000, 0x0000000000010100, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EF60, 0x000055CD7A81EFC0, 0x000055CD7A81EC30, 0x0000000000000001, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EF90, 0x000055CD7A81EFF0, 0x0000000000000000, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EFC0, 0x000055CD7A81F020, 0x000055CD7A81EC90, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81EFF0, 0x000055CD7A81F050, 0x0000000000000000, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81F020, 0x000055CD7A81F080, 0x000055CD7A81ECF0, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81F050, 0x000055CD7A81F0B0, 0x0000000000000000, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81F080, 0x000055CD7A81F0E0, 0x000055CD7A81ED50, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81F0B0, 0x000055CD7A81F110, 0x0000000000000000, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81F0E0, 0x000055CD7A81F140, 0x000055CD7A81EDB0, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81F110, 0x000055CD7A81F170, 0x0000000000000000, 0x0000000000010000, 0x0000000000000000, 0x0000000000000031
,0x000055CD7A81F140, 0x000055CD7A81F1A0, 0x000055CD7A81EE10, 0x0000000000000000, 0x0000000000000000, 0x0000000000000031, 0x000055CD7A81F170, 0x0000000000000000, 0x0000000000000000, 0x0000000000010100, 0x0000000000000000, 0x000000000000DE41
]
nNowAddress=0x55CD7A81E5D0
nEndAddress=0x55CD7A81E810
nStartAddress=0x55CD7A81DEB0
def print_hex(num):
sz=hex(num)[2:]
if len(sz)!=16:
print('0x'+'0'*(16-len(sz))+sz,end=', ')
def print_BYTE(num):
sz=hex(num)[2:]
if len(sz)!=16:
sz='0'*(16-len(sz))+sz
ncount=0
for i in range(len(sz)-1,-1,-2):
print(24+ncount,'0x'+sz[i-1]+sz[i],end=', ')
ncount+=1
def GetToArray(num):
sz=hex(num)[2:]
if len(sz)!=16:
sz='0'*(16-len(sz))+sz
Num_List=[]
for i in range(len(sz)-1,-1,-2):
Num_List.append(eval('0x'+sz[i-1]+sz[i]))
return Num_List
class Address:
m_Index=0
m_PreAdess=0
m_NextAddress=0
m_NextAddess2=0
m_array=[0]*8
m_unused1=0
m_unused2=0
def show(self):
print_hex(self.m_Index)
print(" ",end='')
print_hex(self.m_PreAdess)
print_hex(self.m_NextAddress)
print_hex(self.m_NextAddess2)
print(" ",end=' ')
print(self.m_array,end=' ')
print_hex(self.m_unused1)
print_hex(self.m_unused2)
print()
Address_Array=[ Address() for i in range(len(Num_map)//6)]
nCount=len(Num_map)//6
Size=0
for i in range(0,len(Num_map),6):
Address_Array[Size].m_Index=nStartAddress+i*8
Address_Array[Size].m_PreAdess=Num_map[i]
Address_Array[Size].m_NextAddress=Num_map[i+1]
Address_Array[Size].m_NextAddess2=Num_map[i+2]
Address_Array[Size].m_array=GetToArray(Num_map[i+3])
Address_Array[Size].m_unused1=Num_map[i+4]
Address_Array[Size].m_unused2=Num_map[i+5]
#Address_Array[Size].show()
Size+=1
def FoundFlag(flag,Def_nNowaddress):
if Def_nNowaddress==nEndAddress:
print(flag)
return
else :#
for i in range(nCount):
if Address_Array[i].m_Index==Def_nNowaddress and Address_Array[i].m_array[3]==0:
Address_Array[i].m_array[3]=1
if Address_Array[i].m_array[0]!=1:
FoundFlag(flag+'a',Address_Array[i].m_PreAdess)
if Address_Array[i].m_array[1]!=1:
FoundFlag(flag+'d',Address_Array[i].m_NextAddress)
if Address_Array[i].m_array[2]!=1:
FoundFlag(flag+'t',Address_Array[i].m_NextAddess2)
return
#print(nCount/6)
flag=''
FoundFlag(flag,nNowAddress)
#dtdtdtdtddtatdddtatdtaaatatddddddddtatatdd